PROJECTS ON STEGANOGRAPHY
The art and science of invisible communication is termed as steganography.By employing numerous technologies hiding information can be done in steganography to obtain the desired goals.Projects on Steganography mainly focuses on to send news and information without removing and we can be confident that the messages are being tracked back to us by using steganography.
2015 IEEE PROJECTS ON STEGANOGRAPHY
- Non-Blind Structure-Preserving Substitution Watermarking of H.264/CAVLC Inter-Frames.
- Digital image watermarking based on Super-Resolution Image Reconstruction.
- A novel image zero-watermarking scheme based on DWT-SVD.
- On the robustness of image watermarking VIA compressed sensing.
- Review of Digital Watermarking for 2D-Vector Map.
- Multiple-description coding for robust image watermarking.
- Quantifying the Visual Content Perceived in DCT Coefficients and PKI Based Semi-fragile Watermarking for Visual Content Authentication of Images.
- Blind watermarking algorithm based on henon chaos system and lifting scheme wavelet.
- On the evaluation of wavelet filter banks for wavelet-based image watermarking.
- Improved Web Page Watermarking.
- A VLSI architecture for visible watermarking in a secure still digital camera (S/sup 2/DC) design (Corrected)*.
- Image authentication and restoration by multiple watermarking techniques with advance encryption standard in digital photography.
- Resolving rightful ownerships with invisible watermarking techniques: limitations, attacks, and implications.
- Security Theory and Attack Analysis for Text Watermarking.
- A New Robust-Fragile Double Image Watermarking Algorithm.
Uses of Projects on Steganography
To estimate the message length steganalysis technique is used.
- An attack when detects the presence of message
- Message length estimating components is ignored.
Steganography systems uses the following terminology
Secret key.
Secret message.
Cover message.
Embedding algorithm.
In various methods hiding information within audio files are done,by using least significant bit as modifications does not workwell in audible changes to sounds.High degree of redundancy digital file formats are used for steganography.The bit of an object which provides accuracy greater than the object’s display and use.The most popular method used for steganography is LSB substitution method.On the property of JPEG phase extraction is based to make changes to the image not visible to the human eye.
Rounding errors result in cooefficient data that are not noted during the DCT transformation phase of the compression algorithm.Projects on steganography are being carried out by using all sorts of techniques.Every year we update projects on steganography paper titles from IEEE journals and use support to all B.E and M.E students.
Projects on Steganography :
- Drug dealears
- Media data base systems
- Data altering protection
- Secret data storing and confidential communication
- Access control system for digital content distribution
- Cover communication by executives
To map one symble to one code word Huffman codes are used.Huffman coding assigns a binary code to every intensity value of image and a 2-D M2XN2 image is changed to a 1-D bits stream of length LH
Digital image in bitmap format and compressed image format like JPEG applies still imagery steganography.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
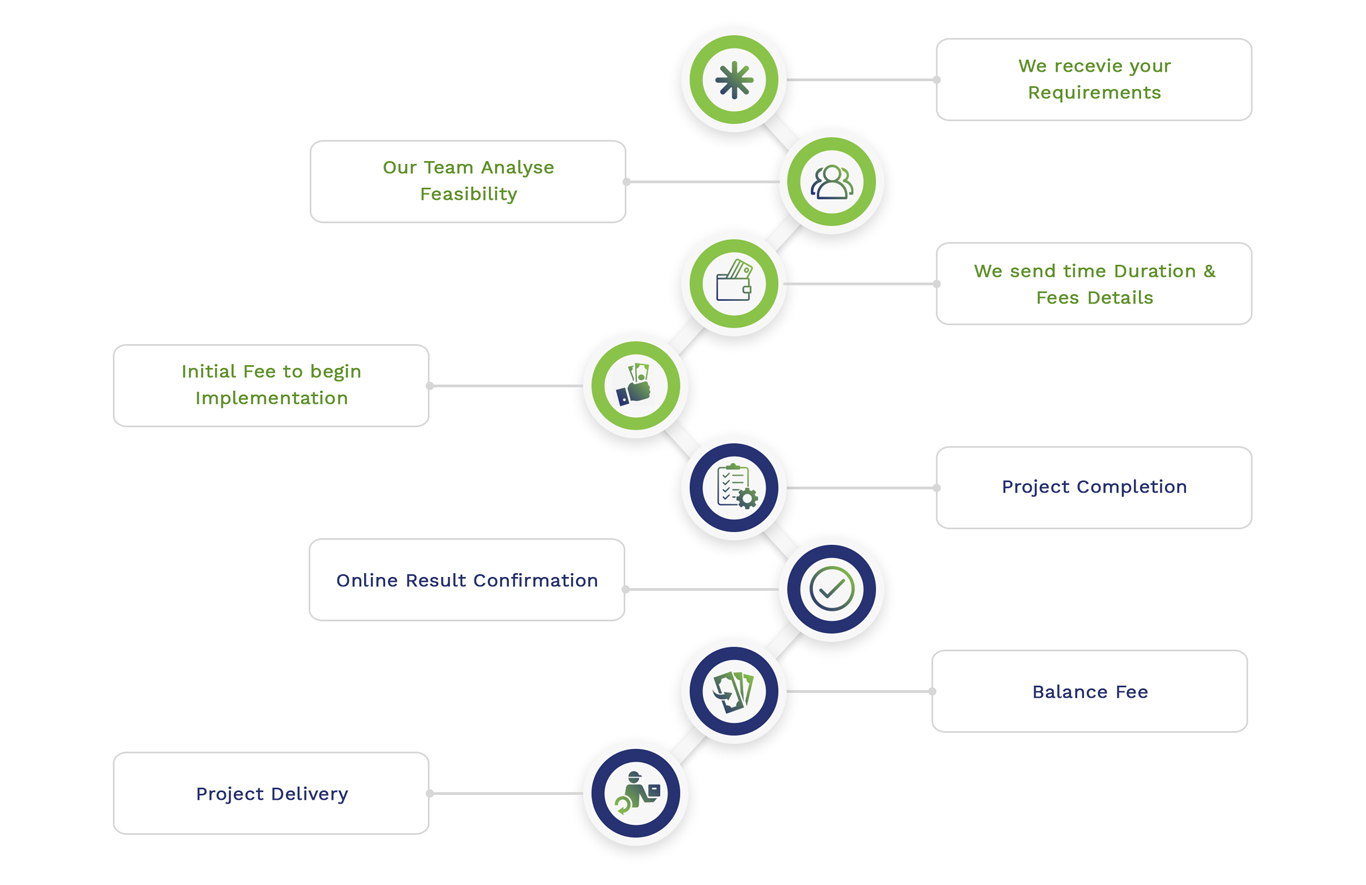
Simulation Projects Workflow
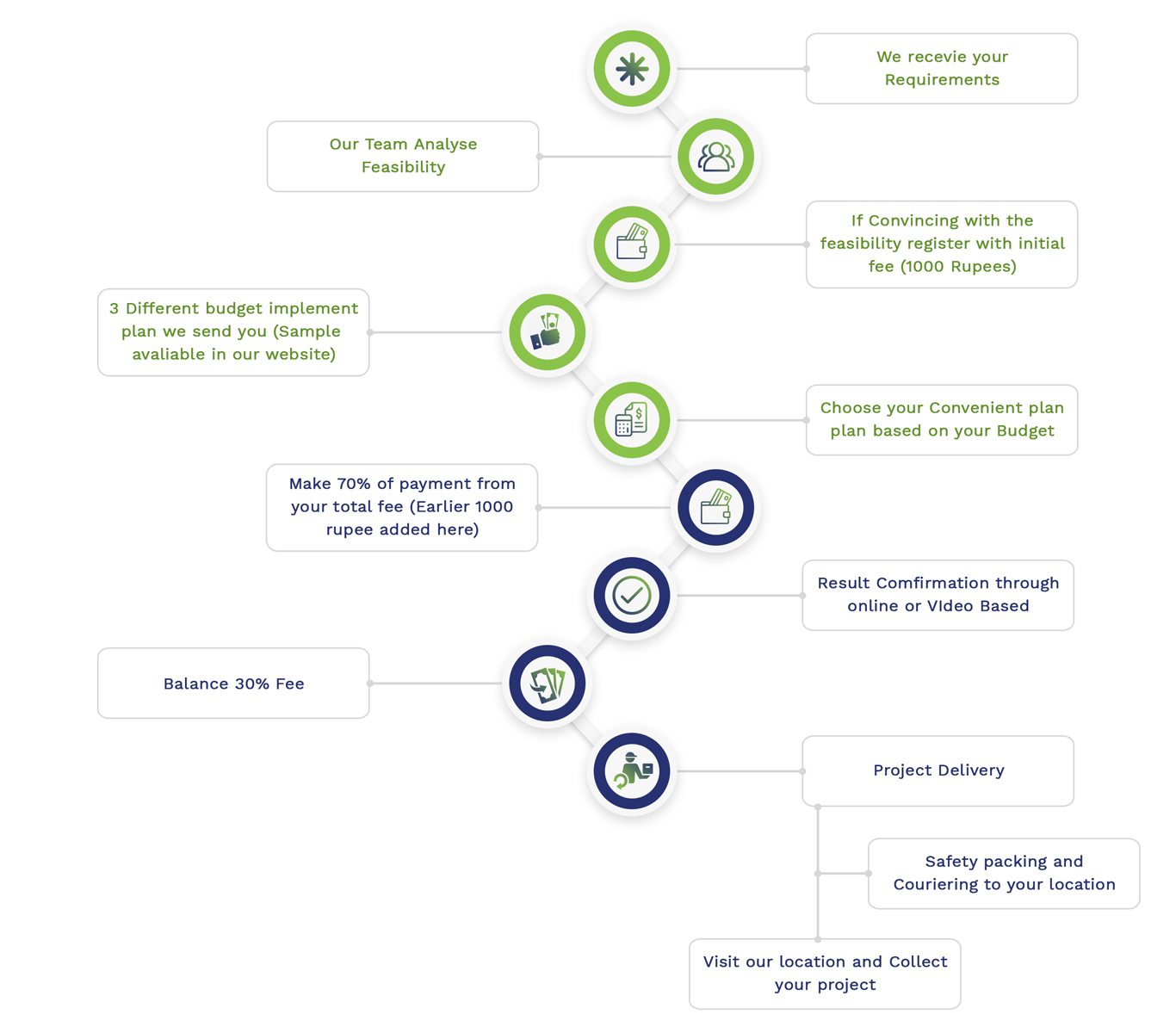
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






