Network security projects
Network security Projects consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, modification, misuse of a computer network.The art of using maths to encrypt and decrypt data is known as cryptography. One can save confidential information or transfer it through various insecure networks that no one views it, cryptography is a part of Network Security Projects.
Basic quality for Network Security Projects
- Authentication
- Confidentiality
- Availability
- Identification
- Integrity
- Non-repudiation
- Non-deny
2015 IEEE Network Security Projects
1.Chaotic Cryptography Using Augmented Lorenz Equations Aided by Quantum Key Distribution.
2.Measurement-Device-Independent Quantum Cryptography.
3.Entanglement Sampling and Applications.
4.Quantum Photonic Network: Concept, Basic Tools, and Future Issues.
5.A High-Speed FPGA Implementation of an RSD-Based ECC Processor.
6.Safeguarding Quantum Key Distribution Through Detection Randomization.
7.Risk Analysis of Trojan-Horse Attacks on Practical Quantum Key Distribution Systems.
8.Fast and Generic Inversion Architectures over GF(2m) Using Modified Itoh-Tsujii Algorithms.
9.Time-Bound Anonymous Authentication for Roaming Networks.
10.Implementation of a New Lightweight Encryption Design for Embedded Security.
11.The Error Tolerance Bound for Secure Multi-Qubit QKD Against Incoherent Attack.
12.Scalable Elliptic Curve Cryptosystem FPGA Processor for NIST Prime Curves.
13.Minimizing Pixel Expansion in Visual Cryptographic Scheme for General Access Structures.
14.Customized Certificate Revocation Lists for IEEE 802.11s-Based Smart Grid AMI Networks.
15.User-Defined Privacy Grid System for Continuous Location-Based Services.
16.Effective Key Management in Dynamic Wireless Sensor Networks.
17. Effectively Exploiting Parasitic Arrays for Secret Key Sharing.
18.High-Speed Polynomial Multiplication Architecture for Ring-LWE and SHE Cryptosystems.
19.Adaptively Secure Identity-Based Broadcast Encryption with a Constant-sized Ciphertext.
20.Secret Communication Using Parallel Combinatory Spreading WFRFT.
Security Measures in Network Security Projects :
- Computational security.
- Unconditional security.
Cryptography and Network security projects
– makes use of two types of keys
Public key is not highly confidential which guarantees that specific key is known to both the parties.
For the purpose of signing messages or private property to a user cryptography makes use of digital signature
Public key principle are
- Authentication.
- Confidential.
- Encryption are authenticated.
Uses of Public key encryption in Network security Projects
- Digital signature.
- Key exchange.
- Encryption /decryption.
Asymmetric-key cryptography is the other name for public –key that can be distinguished from symmetric – key cryptography. One must use algorithm of RSA for asymmetric-key cryptography.
One can use escrowed encryption for a strong cryptography without following crypto anarchy path, which links up strong encryption with an emergency decryption capability based network security project titles.
Benefits of crypto systems in Network Security Projects:
- Under symmetric crypto system if chance’s for data to be intercepted the encrypted data can be moved on the link.
- It is not a necessary for exchanging of keys in asymmetric or public key, which avoids key distribution problem.
- To approve the receivers identity password authentication is used in symmetric cryptosystem.
One can make use of neural network based cryptographic security to choose as networking thesis topics
Neural network parameter values are
- Sigmoid activates function.
- Networks connected fully.
- Input layer of six bit binary input.
- To state the encrypt output message, output layer consist of six bit binary output.
Cryptosystem works towards attacks
- Known plaintext attack.
- Chosen key attack.
- Chosen plain text attack.
- Chosen cipher text attack.
- Cipher text only attack.
- Adaptive chosen plaintext attack.
Internet dealing such as signature verification and legal negotiations make use of digital signatures, which gains high popularity.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
Simulation Projects Workflow
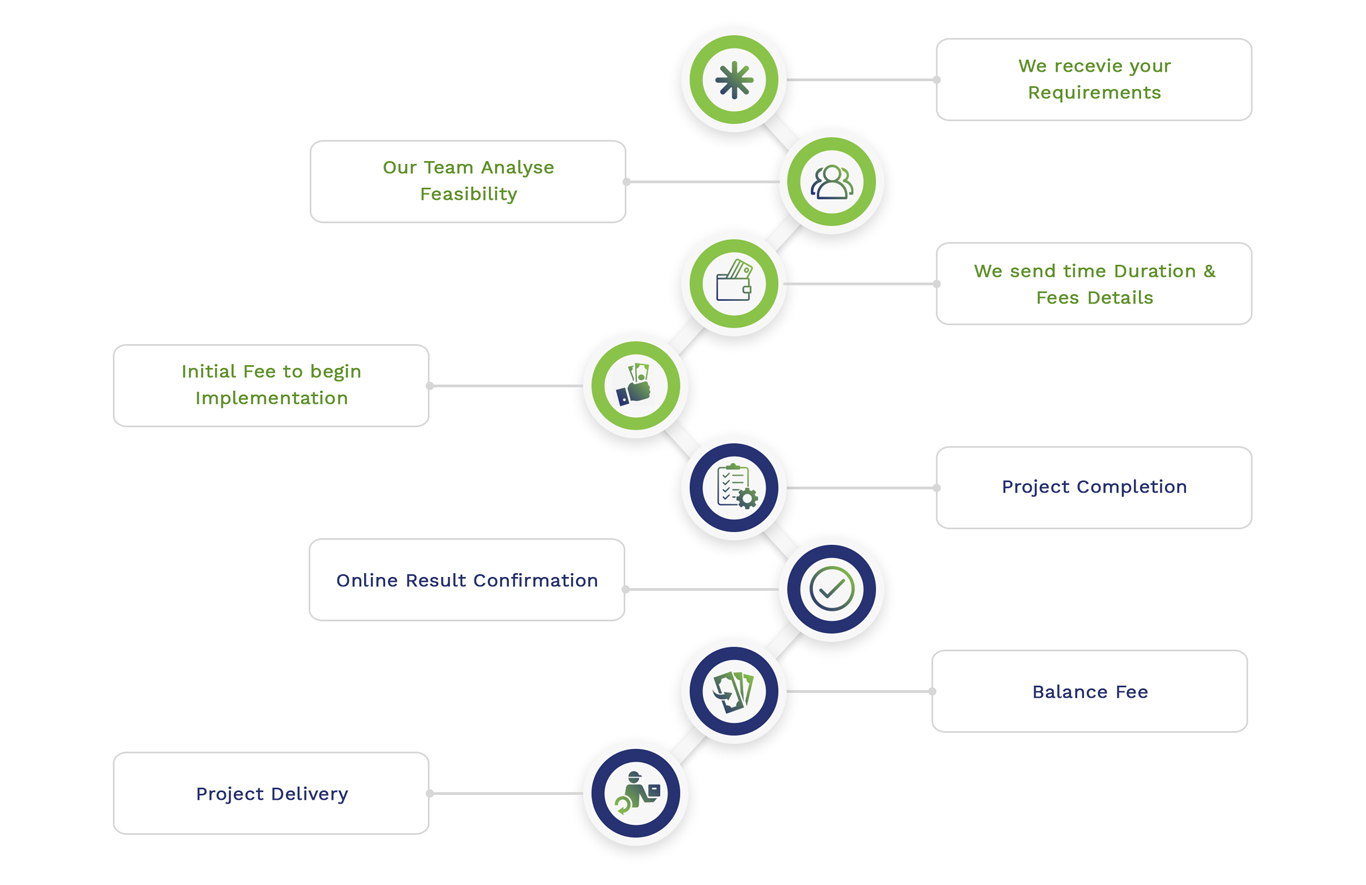
Embedded Projects Workflow
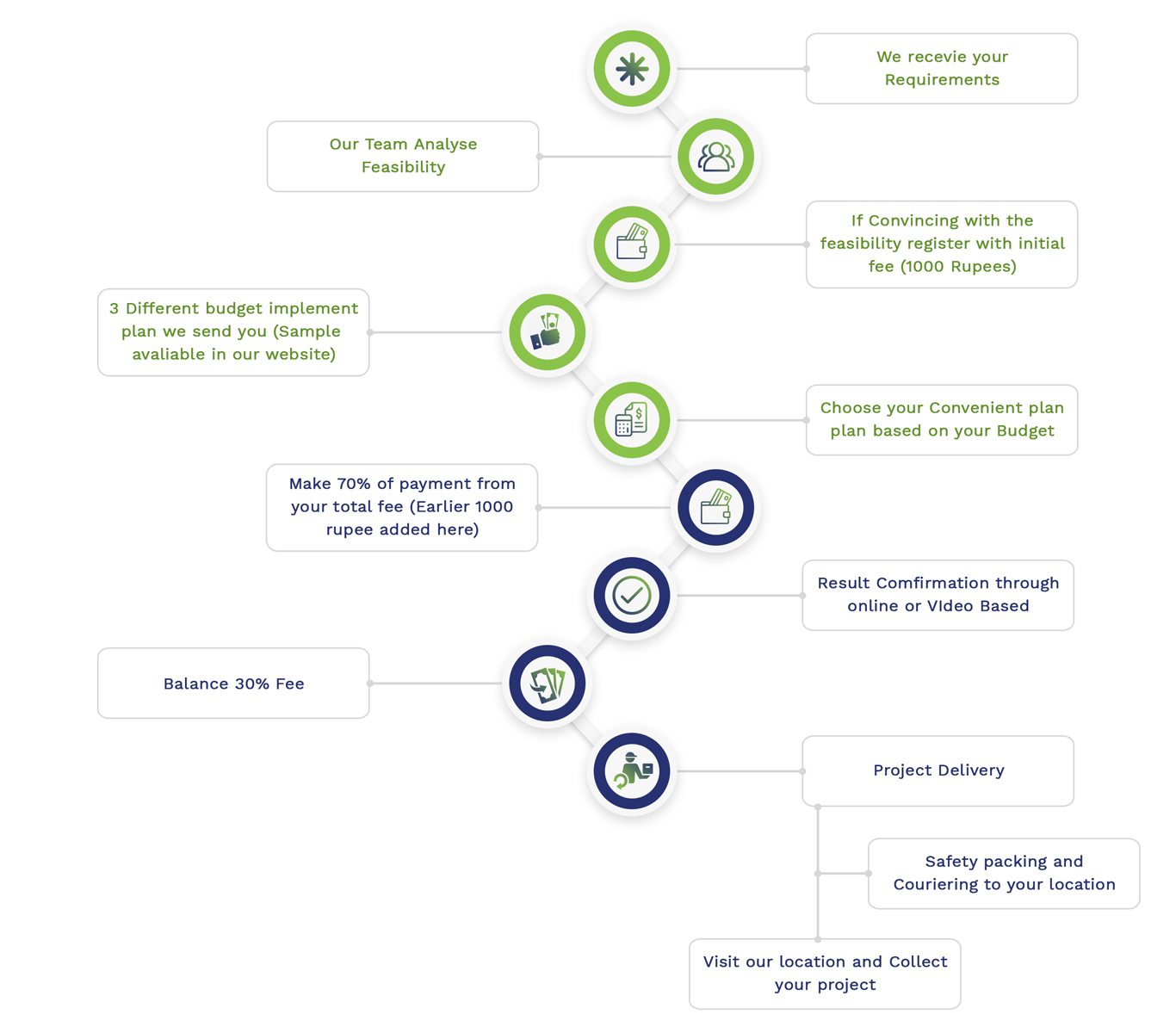


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






