Cybersecurity is considered as an important aspect that aims to protect frameworks and information from external attacks. In terms of different subdomains, we list out various cyber security thesis topics that are both interesting and important in solving current limitations related to cybersecurity:
- Evaluating the Effectiveness of Zero Trust Architectures: In various industrial backgrounds, how Zero Trust safety frameworks are applied has to be investigated. By comparing with conventional network safety frameworks, evaluate the efficiency of Zero Trust safety frameworks in reducing cyber hazards.
- Developing Quantum-Resistant Cryptographic Algorithms: Aim to explore and suggest novel cryptographic techniques that are capable of resisting quantum computing-based assaults. Previous cryptographic protocols are currently vulnerable due to the emergence of quantum computing.
- Machine Learning Techniques for Detecting Phishing Attacks: Specifically for minimizing the extensive cyber assaults occurrence, find phishing websites and emails in a precise manner by modeling and testing methods of machine learning.
- Security Vulnerabilities in IoT Devices: Some general safety risks in Internet of Things (IoT) devices have to be examined. To protect these devices, suggest techniques. In important firms, aim for safer IoT deployment by creating a model.
- The Role of Artificial Intelligence in Enhancing Cybersecurity Defenses: To enhance cybersecurity protections, by considering the processes like actual time hazard identification, forecasting, and automatic reactions to hazards, in what way AI technologies can be implemented are explored in this topic.
- Blockchain Applications for Secure Voting Systems: In creating a reliable and safer electronic voting framework, suggesting strategies to make sure the morality of vote and voter confidentiality and solving possible hazards based on cybersecurity, investigate the benefits of blockchain mechanisms.
- Cybersecurity Policy Analysis for Critical Infrastructure Protection: For securing crucial framework, study and analyze latest cybersecurity strategies. On the basis of comparative analysis with other firms or countries, recommend enhancements.
- Forensic Analysis of Cyber Attacks Using Big Data Analytics: With the intention of finding sources, assault patterns, and techniques for obstruction, create methodologies for the forensic study of cyber assaults by using big data analytics.
- Enhancing Mobile Security for Corporate Environments: For protecting industrial data on mobile devices, explore the issues and strategies like mobile device management (MDM), Bring Your OWN Device (BYOD) strategies, and progression of safer mobile application.
- Social Engineering Attack Strategies and Defense Mechanisms: The psychology in social engineering assaults must be analyzed. Then, intend to find prevalent policies. To aware and secure users, create extensive protection policies.
- Privacy-preserving Technologies in the Age of Big Data: To keep user confidentiality in machine learning frameworks and big data analysis, explore methodologies and mechanisms like federated learning or differential privacy.
- Secure Cloud Computing Architectures for SMEs: In order to fulfill resource limitations and particular safety requirements of small and medium-sized enterprises (SMEs), create safer cloud computing models effectively.
- Ethical Hacking: Techniques and Tools for Cybersecurity Education: Through the interpretation of offensive cybersecurity methods, educate protection policies, for that, a toolkit or educational program has to be modeled for ethical hacking that could be utilized in cybersecurity-based education.
- Assessing the Security Implications of 5G Technology: By concentrating on confidentiality issues, possible risks, and the progression of safety principles for susceptibility reduction, explore the safety problems that are raised due to the 5G mechanism deployment.
- Cybersecurity Awareness and Training Programs: Effectiveness and Improvements: In different firms, the efficiency of previous cybersecurity attention events has to be assessed. To improve cybersecurity practices and ethics, suggest creative techniques or enhancements.
Can anyone give me a pointer on the thesis topic (MSc) cybersecurity?
A topic selection process plays a major role in the research work. Based on various aspects like individual interest, specific domain, and academic requirements, a topic has to be selected. To compress your selections and choose a fascinating MSc thesis topic related to cybersecurity, we offer significant hints and procedures that support you effectively:
- Identify Your Interest Areas
- Initially, consider all the cybersecurity-related topics that you are passionate about. You should think about whether you intend to focus on regions such as human aspects, strategy, or ethical factors of cybersecurity, or you highly concentrate on technical limitations like network safety or cryptography.
- Consider Current and Emerging Threats
- Based on the prospect of cybersecurity, you should consider some current problems. For the exploration process, evolving hazards relevant to quantum computing, artificial intelligence, or IoT devices will be a productive foundation.
- Gap in the Literature
- To find regions that reflect unsolved queries or not thoroughly investigated, you must analyze current publications from more reliable cybersecurity-based conferences or journals. In the latest research, explore gaps that could be addressed by your research.
- Practical Application
- The realistic impacts of your study must be examined. There is a chance to improve your project’s importance and obtain highly effective and promising results, if you are selecting a topic that is capable of solving actual world issues.
- Technical Feasibility and Resources
- On the basis of your contemporary level of expertise, the assistance from your university, and the accessibility of tools or data, evaluate the practicality of carrying out exploration in terms of your selected topic. Particular datasets, mechanisms, or integration with external firms might be needed to deal with some topics.
- Potential for Innovation
- It is essential to explore topics that have an ability to provide opportunities for creativity. To improve cybersecurity, implementation of previous mechanisms in a novel manner, progression of a novel tool, or suggestion of new safety protocol could be encompassed in the creative approach.
- Future Relevance
- You should examine that your study could dedicate to enduring developments in cybersecurity and how this area will emerge in the future era. Aim to select a topic that has a long-lasting relevance and benefits in the specific domain.
Instance Topics to Consider
The following are some topics that provide different insights for research and are considered as important in recent years. Specifically, these topics can assist you to carry out the initial point of your research:
- Creating a framework for secure IoT integration in smart cities
- Evaluating the cybersecurity impacts of remote work trends and progressing instructions for safer telecommuting practices
- Exploring the human aspects in cybersecurity: policies for enhancing cybersecurity awareness and behavior between non-technical users
- The efficiency of AI and machine learning in identifying zero-day vulnerabilities
- The effect of quantum computing on current encryption techniques and the development of quantum-resistant cryptography
- Assessing the confidentiality and security issues of blockchain applications beyond cryptocurrencies, such as in supply chain management or voting systems

Cyber Security Thesis Ideas
PhD scholars often ponder over this question when embarking on their research journey. The key lies in selecting a topic that instantly captivates the readers’ minds, one that is both unique and in high demand within the research community.matlabprojects.org have shared innovative Cyber Security Thesis Ideas read our topics to know more.
- Reliability analysis of cyber security in an electrical power system associated WAN
- Development approach to the attack modeling for the needs of cyber security education
- Cyber-Security Constrained Placement of FACTS Devices in Power Networks From a Novel Topological Perspective
- Stratification of Hacker Forums and Predicting Cyber Assaults for Proactive Cyber Threat Intelligence
- CP-SAM: Cyber-Power Security Assessment and Resiliency Analysis Tool for Distribution System
- A Decade of Studies on Cyber Security Training in Organizations using Social Network Analysis: A Systematic Literature Review Through Keyword co-Occurrence Network
- Research on cyber security Technology and Test Method of OTA for Intelligent Connected Vehicle
- Cyber Security Threat Detection Model Using Artificial Intelligence Technology
- Cyber security considerations of 4G mobile networks as a commuication service in smart grid
- Proactive cyber security response by utilizing passive monitoring technologies
- Research of smart grid cyber architecture and standards deployment with high adaptability for Security Monitoring
- Artificial Intelligence and Blockchain for Future Cyber Security Application
- Towards reproducible cyber-security research through complex node automation
- Multiparameter Outstation Agents for Cyber-Physical Electrical Grid Security and Restoration
- Neural network models in big data analytics and cyber security
- Development and Testing of a Core System for Red and Blue Scenario in Cyber Security Incidents
- Cyber Digital Twin Simulator for Automatic Gathering and Prioritization of Security Controls’ Requirements
- Adaptive event-triggered controller design for cyber-physical systems with complex cyber-attacks
- Digital substation cyber security analysis with SYN-flood attack as a simulation case
- A Second Order Cybernetic Model for Governance of Cyber Security in Enterprises
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
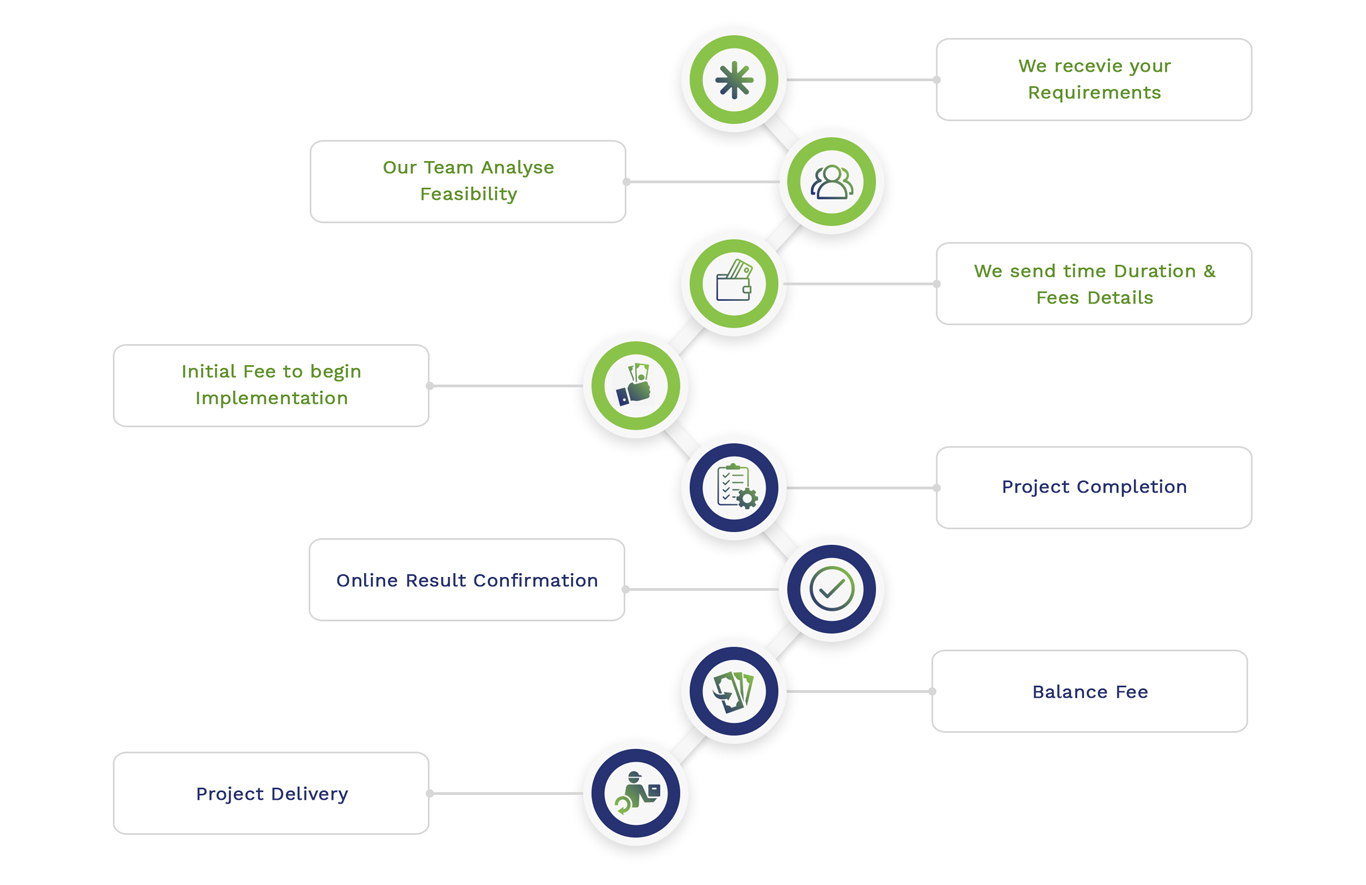
Simulation Projects Workflow
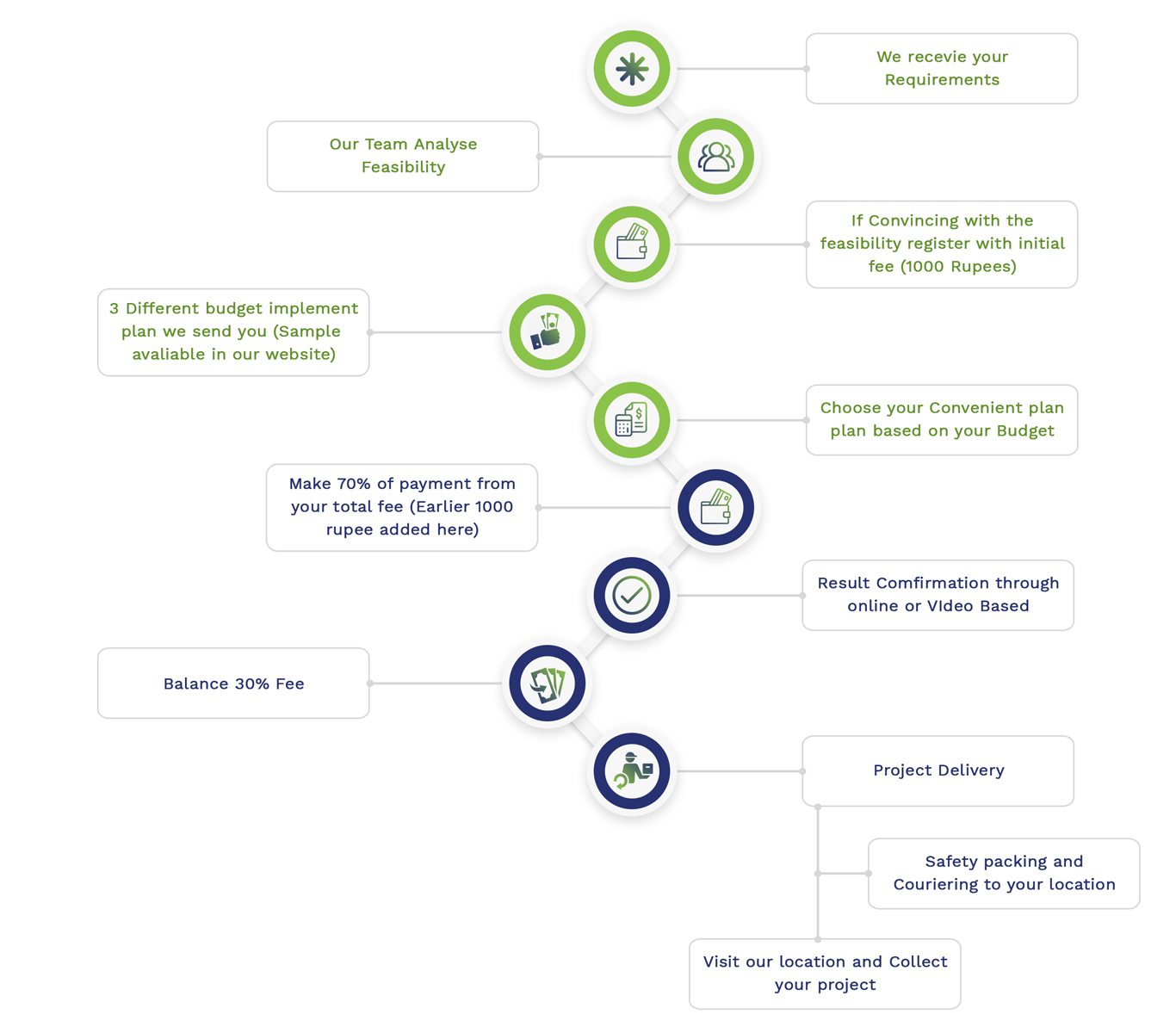
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






