In current years, there are several thesis topics and plans progressing in the field of cloud computing security. A Cloud Computing Security Thesis title should be framed correctly only then it boost up your career, so stay in touch with us to explore more in area of cloud computing. Thesis topics that we share with you will be original and thesis writing will be of high quality. We suggest few thesis topics and plans relevant to cloud computing security that might be more beneficial and efficient for research purpose:
- Advanced Encryption Techniques for Cloud Data Security
Research Aim:
- Appropriate for cloud platforms, aim to explore or enhance encryption methods.
- It is appreciable to contrast the protection and effectiveness of conventional encryption algorithms with progressive approaches such as attribute-related encryption and homomorphic encryption.
Potential Goals:
- An encryption model has to be constructed in such a manner that is capable of offering data integrity and privacy.
- In cloud storage and processing, focus on evaluating the computational overhead and performance influence of modern encryption approaches.
- Intrusion Detection Systems (IDS) in Cloud Computing
Research Aim:
- Mainly, for cloud platforms, it is better to formulate and deploy intrusion detection systems.
- In order to improve the identification of abnormalities and malevolent behaviours, employ artificial intelligence and machine learning.
Potential Goals:
- Focus on creating a hybrid IDS that is able to integrate anomaly-based and signature-based identification.
- Specifically, in detecting cloud-specific attacks, assess the performance of various machine learning methods.
- Privacy-Preserving Data Analytics in Cloud Computing
Research Aim:
- To carry out data analytics on cloud environments without convincing the confidentiality of the user, aim to investigate suitable approaches.
- The purpose of federated learning, differential privacy, and safe multi-party computation has to be examined.
Potential Goals:
- To assure data confidentiality when permitting for extensive data exploration, it is better to apply confidentiality-preserving data analytics models.
- Aim to evaluate the trade-offs among confidentiality security and data utilization.
- Blockchain-Based Solutions for Cloud Security
Research Aim:
- As a means to improve the clearness and protection of cloud services, it is beneficial to make use of blockchain mechanisms.
- In cloud platforms, examine the combination of blockchain for safe data sharing, auditing, and identity management.
Potential Goals:
- Generally, for cloud services, construct a blockchain-related access control framework.
- Based on the utilization of blockchain for data integrity and monitorability in the cloud, evaluate the safety advantages and effectiveness.
- Secure Multi-Cloud and Hybrid Cloud Environments
Research Aim:
- The safety limitations related to multi-cloud and hybrid cloud implementations has to be solved.
- For safe data migration, interoperability, and combined security management among various cloud environments, aim to explore efficient policies.
Potential Goals:
- Specifically, for multi-cloud and hybrid cloud platforms, construct an extensive security model.
- Appropriate tools have to be applied for handling, tracking, and assuring the protection of applications and data among numerous clouds.
- AI-Driven Security Automation in Cloud Computing
Research Aim:
- For computerizing cloud security missions, investigate the utilization of machine learning and artificial intelligence.
- It is approachable to construct frameworks for adaptive security strategies, predictive threat identification, and automated incident response.
Potential Goals:
- For cloud platforms, focus on developing an AI-related safety automation environment.
- In decreasing attacks and mitigating response times, it is significant to assess the performance of AI-based safety criterions.
- Secure Cloud Storage Solutions with Enhanced Data Integrity
Research Aim:
- In order to assure data accessibility and integrity in cloud storage models, aim to examine suitable techniques.
- The utilization of redundant storage, integrity verification protocols, and erasure coding has to be investigated.
Potential Goals:
- A safe cloud storage infrastructure has to be modelled in such a manner that assures data adaptability and integrity.
- In cloud storage models, deploy and assess the effectiveness of data integrity evaluations and recovery technologies.
- IoT Security in Cloud-Connected Environments
Research Aim:
- In IoT models which carry out data storage and processing, based on cloud architecture, the safety limitations have to be solved.
- Typically, for IoT devices in the cloud, investigate safe interaction protocols, data protection policies, and authentication technologies.
Potential Goals:
- To assure end-to-end protection, aim to construct a safe IoT-cloud combination model.
- On the consistency and effectiveness of IoT cloud frameworks, evaluate the influence of safety criterions.
- Risk Management and Compliance in Cloud Computing
Research Aim:
- For handling safety vulnerabilities and assuring regulatory adherence in cloud platforms, focus on exploring tools and models.
- In sustaining safety principles, research the contribution of continuous tracking and automated compliance evaluations.
Potential Goals:
- Appropriate for cloud service customers and suppliers, develop a risk management system.
- To track and implement safety strategies in a consistent way, focus on deploying a compliance automation tool.
- Secure Virtualization Techniques in Cloud Environments
Research Aim:
- Concentrating on VM isolation, secure multi-tenancy, and hypervisor safety, investigate safety limitations and approaches in virtualized cloud platforms.
- The utilization of safe virtualized mechanisms like container safety and hardware-assisted virtualization has to be examined.
Potential Goals:
- In order to reduce hypervisor risks and improve VM isolation, construct a safe virtualization model.
- In avoiding cross-container assaults, assess the performance of container security tools and approaches.
- Access Control and Identity Management in Cloud Computing
Research Aim:
- For cloud services, investigate progressive identity management frameworks and access control systems.
- In cloud platforms, examine the utilization of identity federation, multi-factor authentication, and single sign-on (SSO).
Potential Goals:
- To implement least privilege and dynamic access strategies, aim to create an efficient access control framework.
- An identity management approach which combines with different cloud suppliers and services in a consistent manner has to be applied.
- Distributed Denial of Service (DDoS) Mitigation in Cloud Environments
Research Aim:
- For identifying and decreasing DDoS assaults in cloud platforms, it is appreciable to investigate approaches.
- Focus on examining the utilization of anomaly identification methods and cloud-related DDoS protection services.
Potential Goals:
- A DDoS mitigation model has to be constructed which utilizes cloud scalability and replication.
- In a cloud setting, assess the performance of various DDoS identification and reduction policies.
What are the Research problems in cloud security?
There are several research issues that exist in cloud security discipline. We offer few important research issues in cloud security:
- Data Breach Prevention and Mitigation
Challenges:
- Unauthorized Access: Normally, confidential data could be accessed only by the authorized users. Therefore, assuring this is examined as
- Data Leakage: The malevolent or unintended revelation of confidential information needs to be avoided.
- Data Integrity: At the time of storage and transmission, data sustains to be reliable and unchanged. So, assuring it is crucial.
Research Queries:
- In what way can encryption approaches be enhanced for protection and effectiveness in cloud platforms?
- What are the most efficient techniques for identifying and avoiding violations of data in actual-time?
- Secure Data Storage and Management
Challenges:
- Data Encryption: Mainly, for data at inactive state and during transmission, it is significant to construct and deploy effective encryption plans.
- Key Management: Safe and effective management of encryption keys needs to be assured.
- Data Redundancy and Availability: For accessibility, stabilizing replication by dealing with numerous data copies is necessary.
Research Queries:
- How can homomorphic encryption be efficiently implemented to cloud storage to permit computation on encrypted data?
- What are the efficient approaches for secure key management in a multi-cloud platform?
- Identity and Access Management (IAM)
Challenges:
- Authentication: Normally, safe and user-friendly authentication technologies have to be assured.
- Authorization: In order to adjust to dynamic cloud platforms, it is important to apply delicate access controls.
- Identity Federation: Among various cloud services and environments, the process of handling identities is examined as crucial.
Research Queries:
- In what way can multi-factor authentication (MFA) be improved to offer robust safety without convincing user comfort?
- What are efficient frameworks for federated identity management in a multi-cloud environment?
- Intrusion Detection and Prevention
Challenges:
- Detection Accuracy: To decrease false positives and negatives, it is necessary to enhance the precision of intrusion detection systems.
- Real-Time Response: Specifically, identify and react to safety events in an efficient manner. Assuring that is determined as crucial.
- Adaptive Security: According to progressing attacks, the way of altering intrusion identification technologies are examined as significant.
Research Queries:
- How can machine learning methods be utilized to enhance the identification of complicated cyber assaults in the cloud?
- What are the limitations and approaches for deploying actual-time intrusion identification models in cloud platforms?
- Compliance and Regulatory Challenges
Challenges:
- Regulatory Compliance: It is important to assure that the cloud services adhere to different data protection rules such as HIPAA, GDPR.
- Data Sovereignty: Among jurisdictions by means of varying judicial necessities, handling data is significant.
- Auditability: For adherence usages, offering extensive and clear audit trails are determined as crucial.
Research Queries:
- What are the efficient approaches for assuring adherence to universal data security rules in a multi-cloud arrangement?
- In what way can blockchain mechanisms be employed to improve adherence and verifiability in cloud platforms?
- Privacy-Preserving Computation
Challenges:
- Data Privacy: At the time of carrying out computations on cloud data, it is important to secure user confidentiality.
- Secure Multi-Party Computation (SMPC): Typically, to collaboratively execute an operation through their input without convincing their confidentiality, it is necessary to allow parties.
- Federated Learning: It is crucial to facilitate trained machine learning frameworks among decentralized data resources without compromising the confidentiality of data.
Research Queries:
- How can differential privacy be efficiently combined into cloud computing services to assure data confidentiality?
- What are the limitations and approaches for applying federated learning in cloud platforms?
- Threat Intelligence and Analytics
Challenges:
- Threat Detection: In cloud platforms, it is necessary to detect progressing risks and attacks.
- Threat Intelligence Sharing: Among cloud consumers and suppliers, the process of enabling safe and effective distributing of threat intelligence is determined as crucial.
- Behavioral Analysis: In order to identify abnormalities reflective of safety attacks, user and model activities have to be examined.
Research Queries:
- In what way can machine learning and AI be utilized to improve threat intelligence and pre-emptive threat identification in the cloud?
- What are the efficient ways for safe and effective threat intelligence sharing in a multi-cloud platform?
- Network Security in the Cloud
Challenges:
- Secure Communication: The morality and privacy of data shared among cloud clients and services has to be assured.
- DDoS Protection: Against distributed denial-of-service assaults, it is significant to secure cloud services.
- Network Segmentation: To constraint the influence of safety violations, deploying efficient network segmentation is determined as significant.
Research Queries:
- What are the most efficient policies for reducing DDoS assaults in cloud platforms?
- In what way can software-defined networking (SDN) be utilized to improve network safety and segmentation in the cloud?
- Secure Virtualization and Containerization
Challenges:
- VM and Container Security: It is crucial to assure the protection of containers and virtual machines (VMs).
- Isolation: To avoid cross-contamination, it is important to sustain robust segregation among containers and VMs.
- Hypervisor Security: Generally, the hypervisor needs to be secured in opposition to assaults which might convince the overall virtualized platform.
Research Queries:
- What are the most efficient approaches for protecting containers in a cloud platform?
- How can hypervisor safety be improved to secure in opposition to evolving attacks?
- Blockchain and Cloud Security Integration
Challenges:
- Decentralized Trust: To improve protection and belief in cloud services, it is important to employ blockchain.
- Smart Contracts: In a cloud platform, assuring the consistency and protection of smart contracts are determined as crucial.
- Data Integrity: Specifically, for immutable data storage and validation, blockchain has to be utilized.
Research Queries:
- In what way can blockchain be combined with cloud services to improve belief and protection?
- What are the limitations and approaches for deploying safe and effective smart contracts in the cloud?

Cloud Computing Security Thesis Topics & Ideas
The ideas that we have mentioned below are the hot Cloud Computing Security Thesis Topics so go through it. We are at your service you can call us anytime or drop your details by, mail our experts will you immediate reply. Get customised Thesis Topics that suits your interest, we also share with you the papers that we referred for your project, so all the work will be open. Join us for more success in your career.
- Detecting TCP-Based DDoS Attacks in Baidu Cloud Computing Data Centers
- Strategic management system for academic world: Expert system based on composition of cloud computing and case based reasoning system
- A secure confident cloud computing architecture solution for a smart campus
- Study on a migration scheme by fuzzy-logic-based learning and decision approach for QoS in cloud computing
- A comparative study on various storage techniques in cloud computing
- Access Control in E-Healthcare Records Employing Mobile Cloud Computing Model and Big Data Analytics
- An Effective Framework to Enhance Intelligent Transport Systems using Cloud Computing
- Development of Mobile Learning Software for College English Based on Cloud Computing
- Profile based access control model in cloud computing environment
- Towards efficient and secure access control system for mobile cloud computing
- Algorithms for Big Data in Advanced Communication Systems and Cloud Computing
- Data Security and Privacy Information Challenges in Cloud Computing
- Secure Inter-Cloud architecture for virtual cloud computing based on hybrid IP and MPLS infrastructure solution
- Enhancing Distributed Data Storage Security for Cloud Computing Using TPA and AES Algorithm
- Particle swarm optimization based load balancing in cloud computing
- Collaborative Mobile Edge and Cloud Computing: Tasks Unloading for Improving Users’ Quality of Experience in Resource-Intensive Mobile Applications
- Implementation of Learning Management System Based on Cloud Computing
- Threshold Based Load Handling Mechanism for Multi-Agent Micro Grid Using Cloud Computing
- Performance evaluation of reliable data scheduling for Erlang multimedia in cloud computing
- Dynamic voltage frequency scaling and dynamic network service method in cloud computing by using green cloud
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
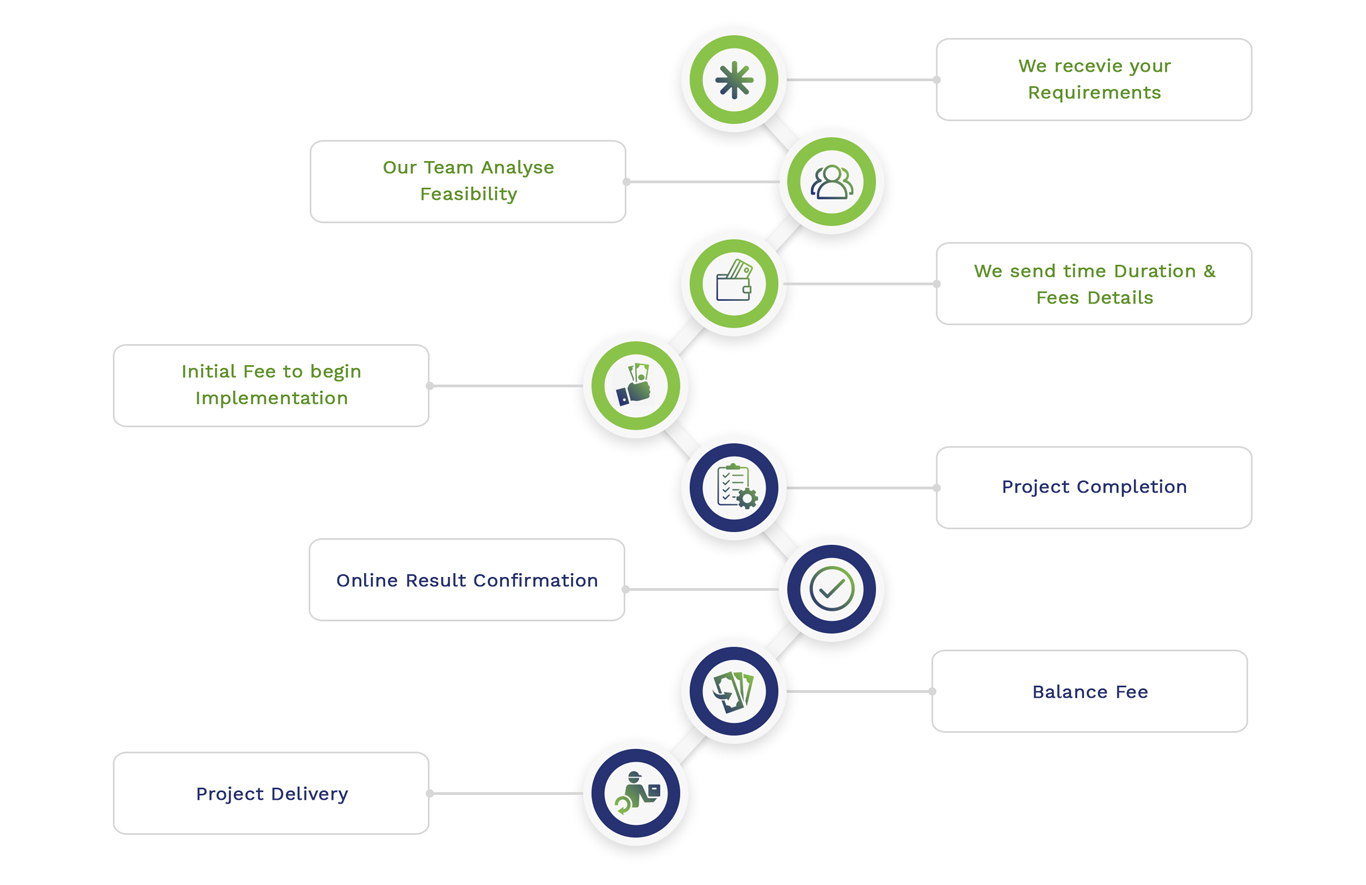
Simulation Projects Workflow
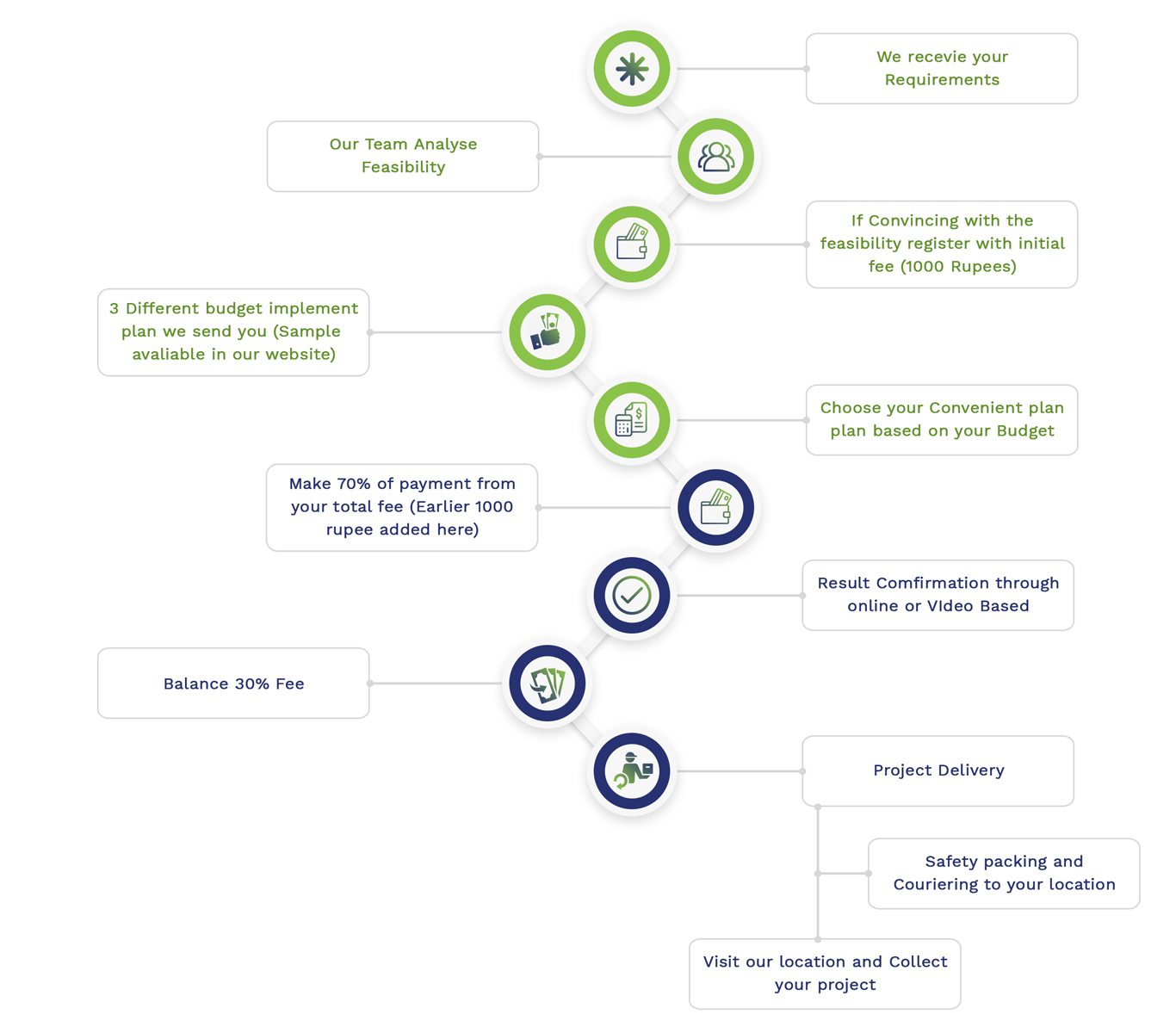
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






