Spatial Mode Side Channels in Free-Space QKD
The quantum key distribution protocol uses one degree of freedom of a single quantum system to encode information. If this information has correlations with the system’s other degrees of freedom, or if the measurement efficiencies on the receiver side depend on them, a security loophole called side channel is created.
An eavesdropper can exploit it to gain information without disturbing the system, and thus, without revealing the attack. Here, we analyze side channels in a free-space QKD sender and receiver implementation and focus especially on the dependencies and side channels for the spatial degree of freedom.
Similar IEEE Project Titles:
- Postprocessing of the Oblivious Key in Quantum Private Query.
- New Regular Radix-8 Scheme for Elliptic Curve Scalar Multiplication without Pre-Computation.
- Automatic Application of Power Analysis Countermeasures.
- Security Considerations in Minutiae-based Fuzzy Vaults.
- Collusion-Tolerable Privacy-Preserving Sum and Product Calculation without Secure Channel.
- Weaving an Assurance Case from Design: A Model-Based Approach.
- Compressing Sets and Multisets of Sequences.
- Authentication protocol for an ambient assisted living system.
- Security for the Internet of Things: A Survey of Existing Protocols and Open Research issues.
- Maximum Information Release While Ensuring Opacity in Discrete Event Systems.
- Software Puzzle: A Countermeasure to Resource-Inflated Denial-of-Service Attacks.
- Fault Attacks on STRNGs: Impact of Glitches, Temperature, and Underpowering on Randomness.
- A Framework for Secure Computations With Two Non-Colluding Servers and Multiple Clients, Applied to Recommendations.
- VProof: Lightweight Privacy-Preserving Vehicle Location Proofs.
- New Parallel Approaches for Scalar Multiplication in Elliptic Curve over Fields of Small Characteristic.
- A Proxy Identifier Based on Patterns in Traffic Flows.
- Secure Spatial Top-k Query Processing via Untrusted Location-Based Service Providers.
- High-Throughput Low-Complexity Systolic Montgomery Multiplication Over GF(2^m) based on Trinomials.
- Space-efficient Verifiable Secret Sharing Using Polynomial Interpolation.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
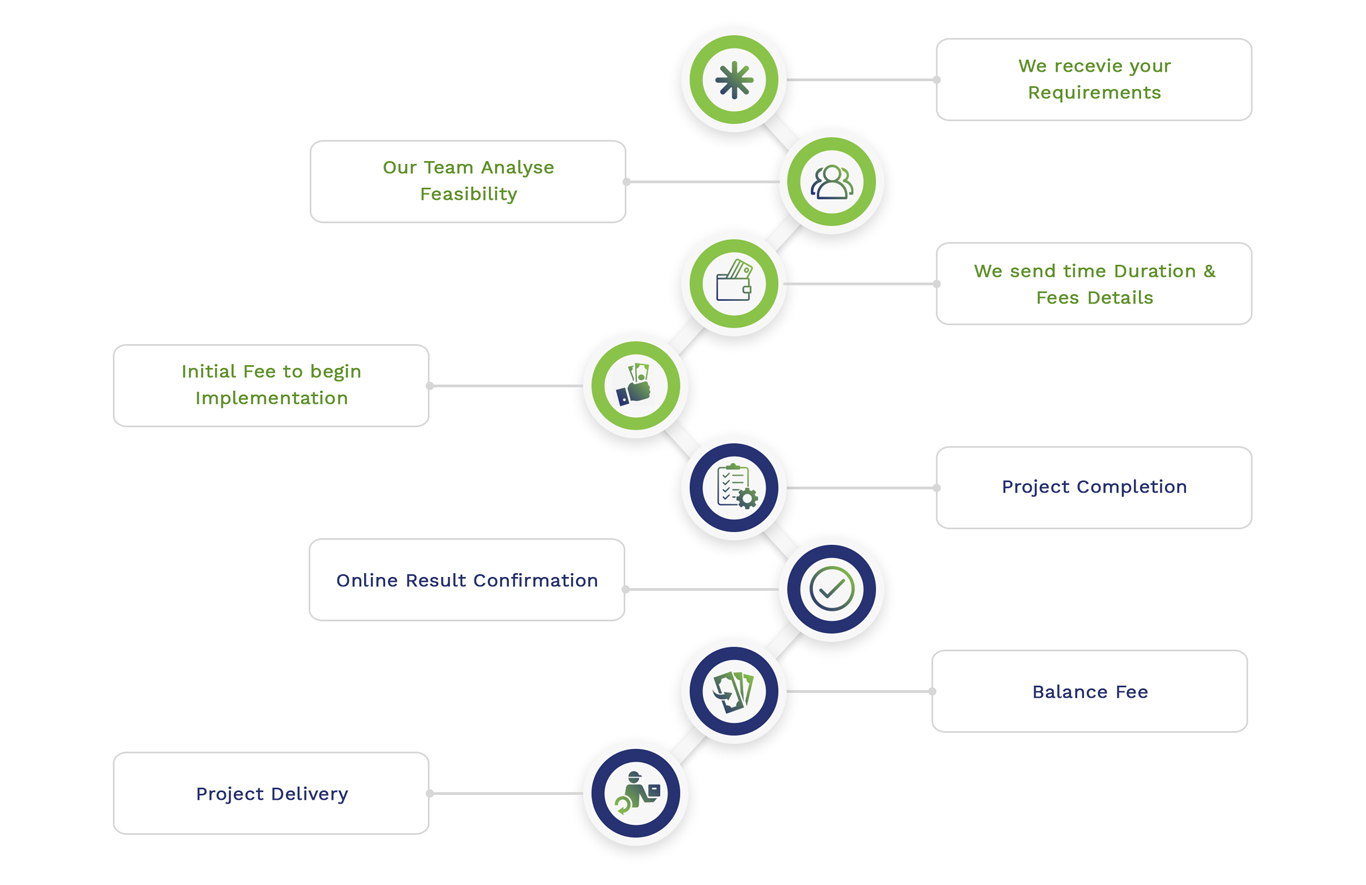
Simulation Projects Workflow
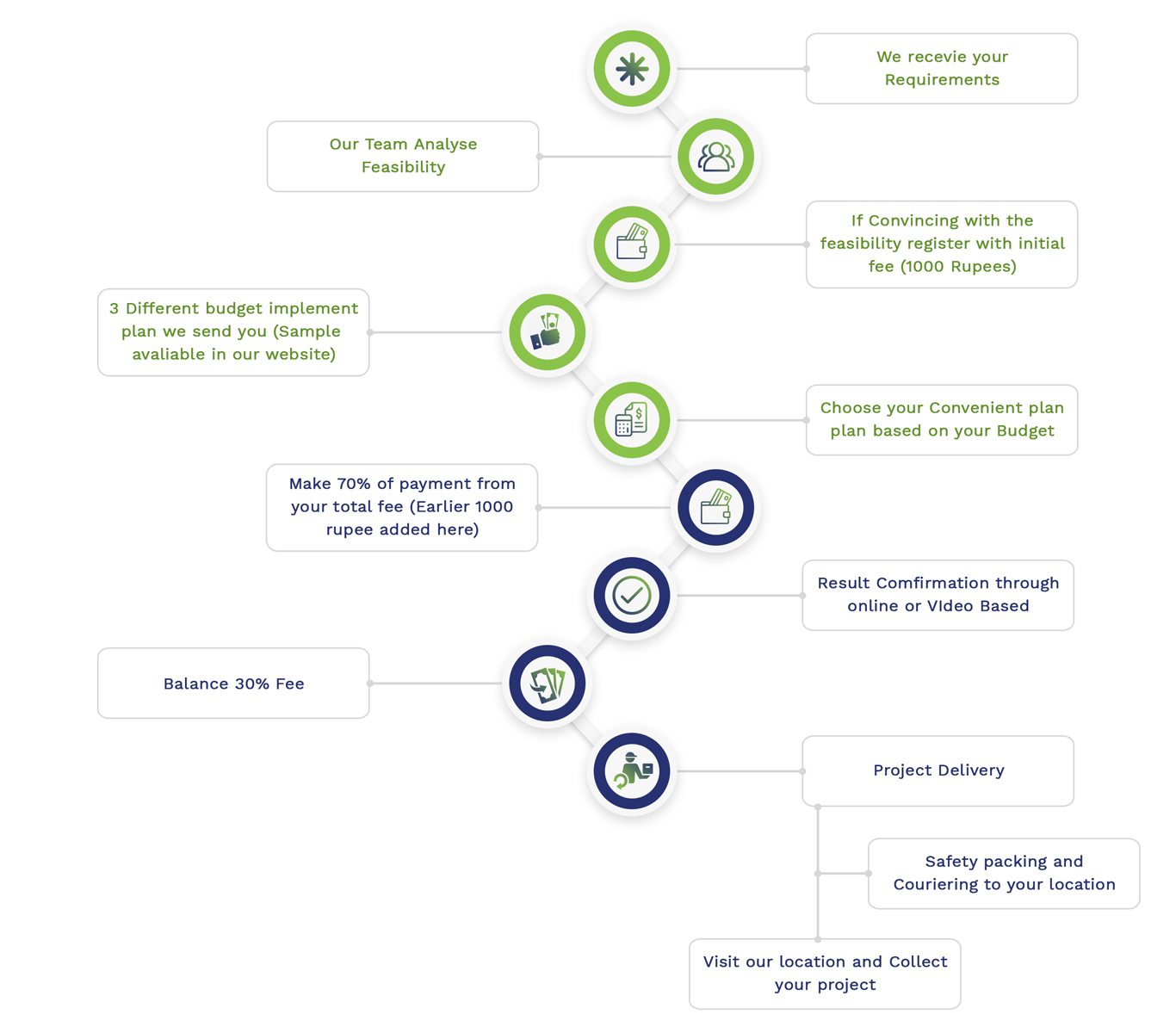
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






