This article attempts to open up to stimulate your choice over the relevant field and to offer you more innovative ideas about dissertation cyber security. The primary function of the information in a system is to confirm the device’s privacy and security. Cybersecurity is the process of preventing harm to the system or networks by unverified use and re-establishing the electronic data and communication systems. It also involves the security and re-establishment of whatever the medium of the network like wired or wireless, satellite. The classifications of security fields enclosed in cybersecurity are as follows:
- Application security

- Data security
- System security
- Functioning security
- Adversity security
- End- user Instruction
The above fields are involved in cybersecurity. So guiding dissertation cyber security induces the vast chances of the scholars and students to get more knowledge about the relevant field. We provide you more about the functions of cybersecurity, its mechanisms, and further platforms.
How does cyber security works?
- Applying threat managing actions
- Fixing structural aims and goals
- Detecting environments
- Computing efficiencies
- Testing and analyzing threats
The main aim and scope of the cybersecurity model are to detect and mitigate the attacks in the environments. All these attacks are harmful, and early detection and prevention of them are necessary to avoid any data / economic / privacy loss. The cyber-attacks and their countermeasures are following,
Cyber Security Attacks and Counter Measures
- Attacks: Breaching Encoded Information, Man in the Middle, Spyware Installation, doxxing.
- Counter Measures: Authenticate Access, encryption, biometric Confirmation.
- Attacks: web Penetration, Unauthorized scans, remote controlling
- Counter Measures: Identifying intrusion, Cryptography, Hashing
- Attacks: DDoS attacks, Ransomware Attacks, Server disruption
- Counter Measures: Regular Backup, Data Replication, Adequate communication and bandwidth.
Types of cybersecurity attacks (Insider Threats)
Apart from the attacks by the hackers, there occur some internal security threats as,
- Industrialized spying
- Exploitation of data by authorized users
- Data leakage by third-party vendors
- Unintentional data leakages
There is a wide range of solutions available to encounter cyber threats. We mentioned some of the previous, and also here, we suggested few methods for detecting insider threats based on malicious activities. The external sources or access does not only cause cyber threats. Without our knowledge, we would be the reason to leak our data sometimes. By implementing and assuring the following actions, we can prevent both internal and external cyber threats.
What are the ways to control cyber threats?
- Authorization: It permits access only to the authorized devices and users to the system
- Controlling access: It ensures only the authentic users can enter into the network to perform sensitive data access
- Verification / Authentication: It verifies the level of access to a device or a network has the privilege to link with the device for computer security. Ensure that all the systems give effective verifying process to prevent security breaches. For instance, if every Internet of Thing systems are produced by the same maker, and organized with the equivalent verification credentials, one system’s security breaching would lead to the concession of all protection phase at the level of data.
- Limiting the number of private users: By this action, you can limit the number of privacy users like, creating user password and ID only to the regular individual who uses the system to avoid the insider threat. Therefore, you can modify or limit the granted access and you can minimize their right to access the system.
- Sensitive Data Access Control: It is important to launch extra level of security login and regularly reviewing the user’s entry to test their roles, privilege to access the data. Assure that the system permits only the authorized users to access the data and assets. Applying just-in-time privacy access administration would lower the risks of hacking.
- Observing the activities of the users: In an organization, it is important to observe the activities of the user. Software that monitoring users activity, delivers video recording on the entire user action and it permit you to see even their current activity and it helps you to detect doubtful activity.
- Define Robust / Reliable Access Policy: It is nothing but providing your employees a list of instructions to follow. This policy is considered to be more important than anything that avoids manual errors and misinterpretations and it also improves existing protection controls.
The actions taken to lessen the risks may vary, but the fundamentals of the protection remain identical. According to the cyber threats behaviors, vulnerabilities, and risks, a cybersecurity mechanism is used. Some of the familiar and effective schemes in cybersecurity are as follows.
Major Cybersecurity Mechanisms
- Random Number Generators
- Threat Detection Systems
- Customized Encryption Tools
- Hardware Protection
- Lightweight Cryptography
Other than the mechanisms mentioned above, there are two other important cybersecurity demonstrations to identify threats and modify the cyber risks. Specifically, in cyber-attacks, prevention is better than anything. Except for prevention, the administration can eliminate or curb the widespread, possible assaults by observing the system’s weakness, unverified entree, and fishy activities.
Cyber Threat Mitigation Approaches
- Preventing Data loss
- Isolating the valuable information or assets from the unverified users is a best suggestion for every field, particularly for the companies that gathering and stocking the customer data. Improving the information backup and data loss prevention system can aid to minimize the sudden threats caused by ransomware, malware etc.
- Vulnerability Management
- This type of defense deserves a crucial importance to save the network, device or system from potential threats. The adversaries often control zero-day activities, vulnerable validation and they use the activities of unskilled users for their criminal activities. Systems / devices can stop such threats or launching base by the hackers, by the frequent update
Based on the handpicked topic of Dissertation cyber security and its functions, prevention of cyber-attacks, etc., we are happy to lead you to the trending topics yet to be researched in cybersecurity.
Research Topics in Cyber Security
- Security and privacy for Vehicular Cloud Computing
- Threat modeling for Security Assessment
- Security of industrial Control systems
- Security Issue and Challenges for CPS
- Towards a Framework for Assuring Cyber Physical System Security
- Security and privacy for Networked Multi-agent CPS
- Security in Cloud-based Cyber Security Model
- Security challenges in Next Generation CPS
- Security Architecture in Cyber Physical systems
Along with providing the latest research topics, we also deliver you the scholarly steps to be followed in dissertation writing and the methodology of discussing the relevant field as follows.
“Dissertation is a complete study of your research which describes the significant information about the methods, techniques used, results achieved and summary of it.”
What are the steps in effective dissertation writing?
The number of steps is used to write effective dissertation writing, which must be precise to make in a clear, understandable form. Some of the significant steps in dissertation writing can be as follows.
- Motivation and problem identification must be a discussion of why you choose the selected topic and its necessity in current scenario to find a result
- Purpose of the solution gathers the aim of the solution from defining the problem and informing what is probable to implement the solution practically
- Design and development this process involves structuring the thesis as a proper research article.
- Demonstration includes validating the possible practices of the article to decipher one or more events of the chosen issue
- Evaluation monitors and tests how much the research article upkeeps the project finding to the relevant problem.
- Final Verification interconnects the progress of the research and its outcomes at the end of the research by verification of both Grammar and Plagiarism.
To conclude, we demonstrated the crucial information about cybersecurity and dissertation writing. If you need more information about it, you can contact our expert’s team. We are interested in solving your research queries and services with your needs.
Throughout your research journey in cybersecurity, we are glad to offer you 24/7 customer service and assure your data confidentiality. We also provide you online PhD guidance so that you need not hesitate to step out to work with us at any level of your project. We are on your deeds and expectation. Working with us would provide you with an amazing experience on your Dissertation Cyber Security, and we ensure your expected result outcomes.
Don’t miss the opportunity to work with our expert research team of certified engineers.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
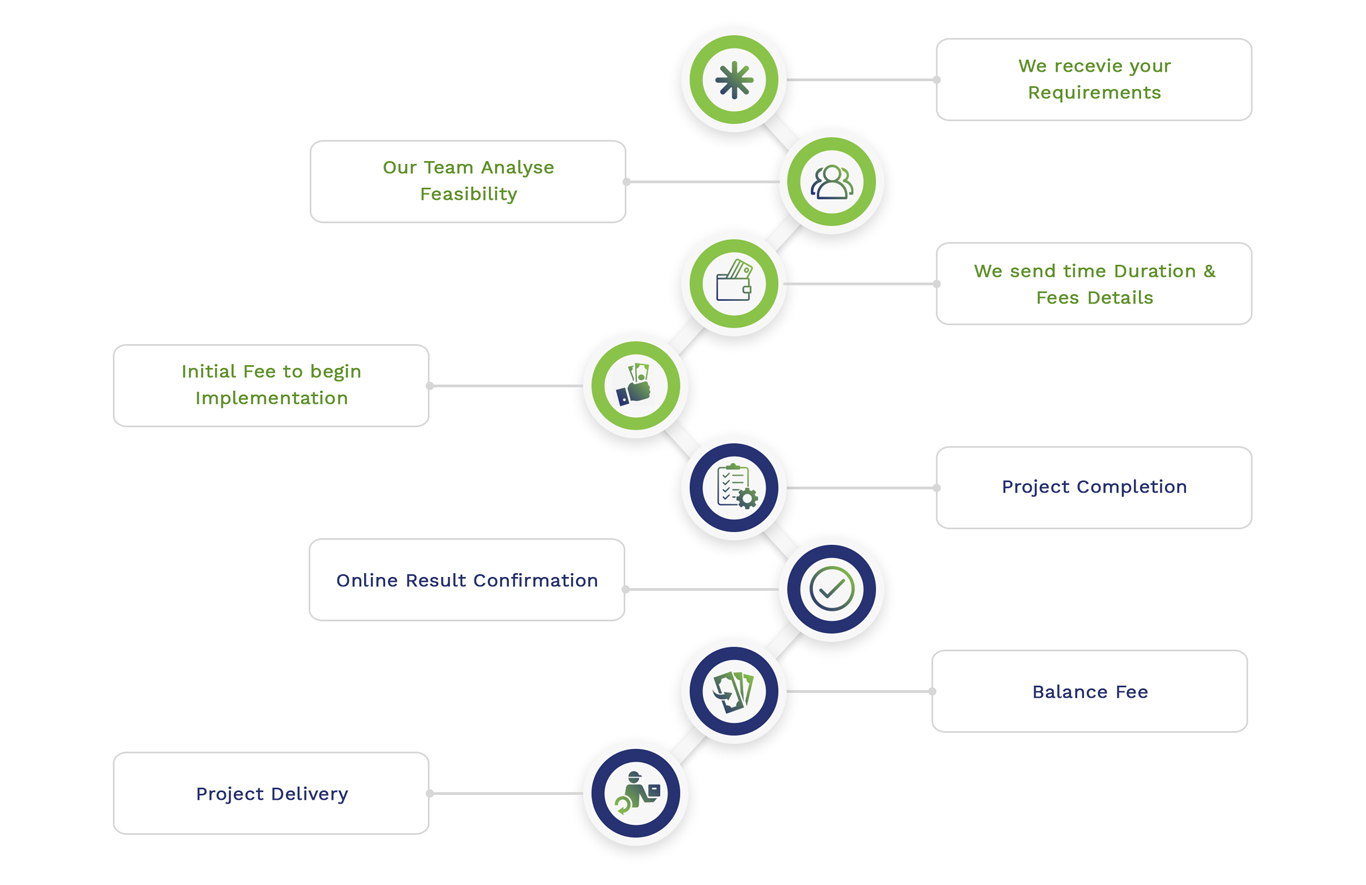
Simulation Projects Workflow
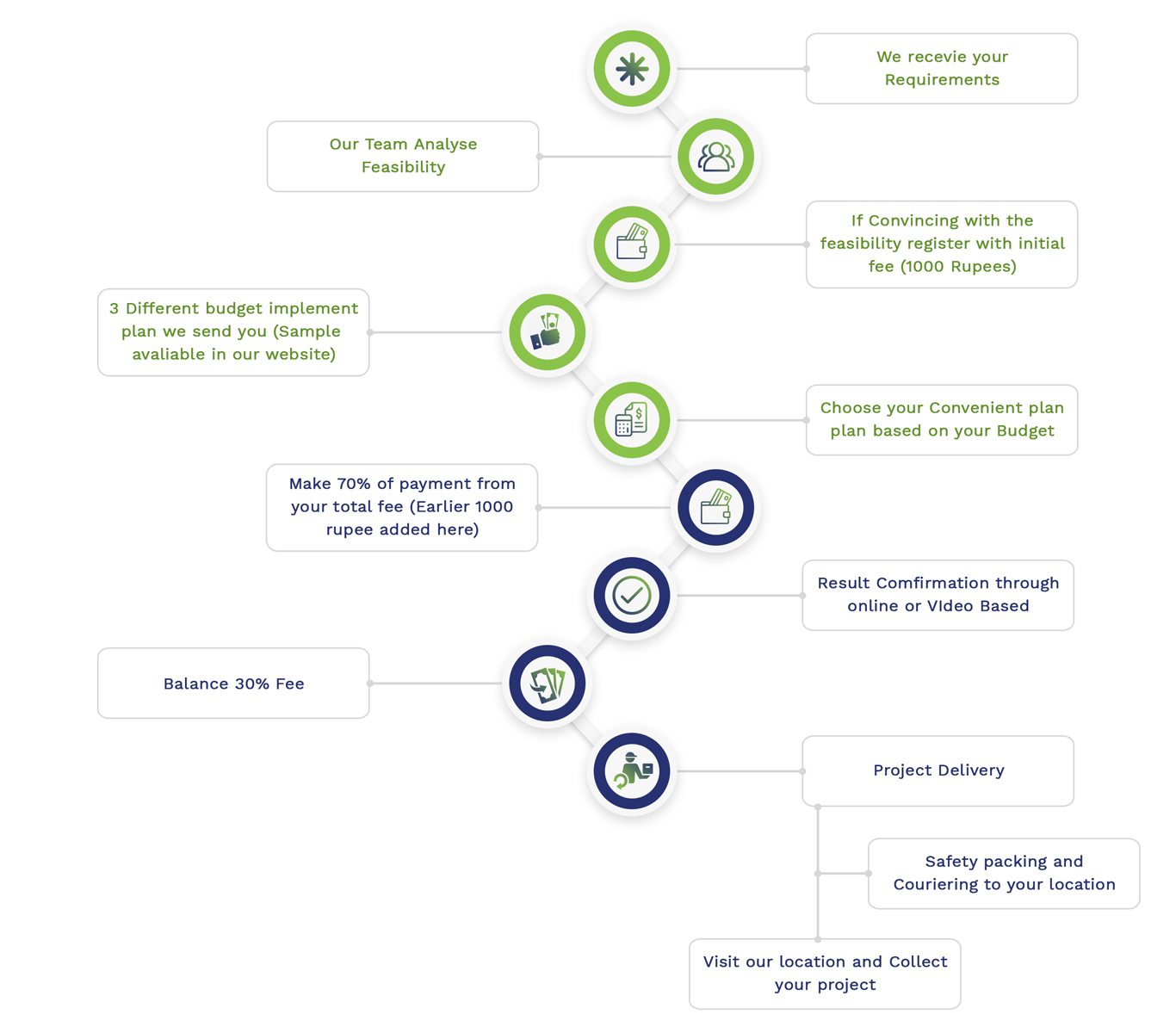
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






