Nowadays, computer networks and other systems are highly prone to attacks once it is linked as a part of a network. We at our company by sending of more computer security project ideas, which are primarily focused on preventing the following attacks from harming the system.
- Infection by dangerous computer data
- Infections by malware (along with scanning)

- Scams due to phishing
- Botnets and Outbound spam
- DDoS or distributed denial of service attacks
In general, computer security is defined as the following.
- Protection of networks / computers / systems
- Safeguarding the applications/services
- Part of network security / cyber / information / computer
The security breaches happening in a network or in a computer within a network are an undesirable indication of the misuse of certain unavoidable vulnerability provisions within it. Finding solutions to such faults is the challenge in front of researchers. Under the computer security project ideas, we have been rendering our sincere guidance to researchers to have a noteworthy career. This article will guide you through computer and network security research and projects where our focus mainly lies on different aspects of it. Let us first start with the issues in computer security.
COMPUTER SECURITY ISSUES
The problems with computer security are confined to various layers of the system, as mentioned below.
- Transport layer – security and authentication of encryption of data and communication (end – to – end)
- Link layer – MAC protocol protection and rendering support to link layer
- Application layer – detection and prevention of abuses, worms, viruses and threats (codes)
- Network layer – forwarding protocols and ad hoc routing protection
- Physical layer – prevention of jamming (and services related to denial of service) in signal
Generally, researchers should focus on identifying the motive that tries to subvert the security system established by an organization or institution. Thereby the potential threats can be easily identified. After identifying the threat, the next step is eradicating it and recovering the system to its normal functioning very quickly. In this regard, letters now try and understand the major aims of computer security systems.
WHAT ARE THE GOALS AND PRINCIPLES OF COMPUTER SECURITY?
The major objectives of a computer security system are listed below,
- Availability: Denial of service attack prevention and ensuring regular and authentic data access
- Integrity: data modification in an unauthorized manner is to be prevented
- Confidentiality: data access by non-authentic sources (processes, entities and individuals) must be stopped
The goals of security, as pointed under the following heads, are the potential research areas.
- Management and authorisation of passwords
- Analysis and audit logging
- Integrity in writing code
- Testing and validation of data
- Sanitization and data validation
- Management and authentication of roles
- Network security
- Data protection
- Cryptography (along with key management)
- Analysis of third party components
The constitution of a security system becomes questionable when at least one of the above aspects is compromised. Usually, researchers like us are sought by researchers primarily during the designing phase of their computer security projects. They would be facing difficulty in ensuring that all these goals are met. As we have been seeing researchers approaching us in this way, we strongly suggest you get to interact with our experts at an earlier stage so as to avoid frustration. We have assisted more than 150+ novel IoT research proposal. In the following section, let us talk about the different steps involved in achieving computer security project ideas.
WHAT ARE SOME STEPS TO ACHIEVE COMPUTER SECURITY?
Consider the following points, which are the basic steps in establishing highly secure computer networks.
- Establishing the mechanism for access control
- Identification of network level designing
- Requirements identification (in relation to each host)
- Resources identification
- Network architecture related requirement identification
The steps mentioned above are the different aspects of computer security that evolved over time. Since the use of wireless networking into the computer for communication, the possibilities of threats and cyber-attacks have been racing. Usually, our experts increase the motivation of researchers to carry out advanced and future studies in their field by encouraging novel ideas. We also brought out many novel thoughts of researchers successfully into reality. Now let us talk about the kind of computer security that is demanded.
WHAT COMPUTER SECURITY IS REQUIRED?
By the term computer security, what is meant actually is protecting user data which is primarily their privacy. So securing user privacy revolves around its safeguard under various network components and processes.
- Processing privacy: It is dependent on integrity of communication and components. Information has to be safeguarded from third party attackers
- Storage privacy: Based on the amount of data to be stored, the privacy of data in various devices have to be maintained
- Communication privacy: Device availability, reliability and integrity affects the privacy of the system. The components of internet of things network can be included in the communication only when it is absolutely necessary
- Device privacy: Critical data can be either lost or leaked due to theft as a result of side channel attacks
Much of the research in computer security has become successful by orienting itself to privacy protection, as mentioned above. The list of our successful projects also involves many computer security project ideas related to managing user data and privacy. Get in touch with us to have detailed practical explanations on various aspects of our projects on computer security. Now let us look into the methodologies involved in ensuring the safety of the computer.
WHAT ARE THE FIVE SECURITY RISK METHODOLOGIES?
The security mechanism should be strict towards unauthorized attacks while allowing the system to function smoothly under a certain threshold risk level. The following are the five methodologies followed by any network security system.
- Identifying the risk
- Exactly predicting the risk that requires to be strictly regulated
- Proper tracking of risk reduction process until it is either removed or decided to be accepted
- Risk reduction budgeting (and planning)
- Assessment of risk (on the basis of its repetition and impact)
When cyber-attacks are made, they attract strident opposition from the established cyber security system based on the aforementioned methods. The only point to note here is that the reaction of a security system can be customized. Here we quickly remark that our technical experts are highly experienced and qualified in carrying out customer research. So you can reach out to us regarding any kind of technical advisory. We are sure to help you. Now let us talk some more about the attacks and vulnerabilities to computer security
COMPUTER SECURITY VULNERABILITIES AND ATTACKS
Access to the network from a non-authentic or unauthorized source is a very common attack. An attacker uses the hub (or a switch port) that is not secured to have access to the network. So usually, the reliability on wired networks is much higher than on wireless. This is because wireless networks are prone to the following attacks
- Packet sniffing (resulting in data theft)
- Spoofing the legitimate physical identities (leading to man in the middle attack)
- Issues related to denial of service (deploying unnecessary packets to flood the network)
Accordingly, there are a lot of methods implemented successfully by researchers around the world as great solutions to the above problems. We gained a huge customer base with respect to the prompt solution mechanisms that we devised to solve the above problems to craft computer security project ideas. Now let us have a quick recap on the entry points and the methods used by the attackers.
WHAT ARE THE MOST COMMON WAYS TO ATTACK VECTORS?
- Accessing networks and service without getting authorization
- Acquiring user password and repeatedly use wrong passwords
- Evaluating the novel security systems
- Assessing the security breaches in the history (when exploring strength of the network is removed completely)
- Verification of security aspects (without bypassing them)
- Overall evaluation by efficient auditing (for enhancing the existing security system)
The response of the security system towards any attack includes the following aspects.
- Identification of the cyber security attacks
- Mechanism for prompt action – containing and eradicating security issues
- Situation investigation
- System for connectivity and data recovery
It is quite likely for researchers to use the latest technologies into the security mechanism in its different aspects as mentioned above. Your substantial interests in computer security can expand beyond the horizon with the guidance for cyber security dissertation from our experts.
TOP 5 COMPUTER SECURITY PROJECT IDEAS
Let us now see the trending computer security research topics.
- Access control (attribute based)
- Fine grained resource access (control based on roles)
- Authentication based on multiple factors
- Compulsory access control
- Decentralized management for threats storage (example: blockchain)
For project guidance and research support on any of the above computer network project topics, you can contact us at any time. Our customer care support team will take you to interact with our experts. Now let us see the different mechanisms involved in ensuring computer security.
WHAT ARE TYPES OF COMPUTER SECURITY MECHANISMS?
The following are the major mechanism used in any network or computer security system.
- Access control
- Integrity of data
- Stuffing bits
- Digital signature
- Encipherment
- Notarization
- Exchange of authentication
Therefore, for establishing a strong computer security system, the mechanisms mentioned previously have to be given more importance. In relation to this, we take customers’ takedown requests from time to time and ensure that all their viewpoints are accepted and supported. Now let us see about the major techniques used in computer security researchers these days.
IMPORTANT TWO METHODOLOGIES FOR COMPUTER SECURITY
From our two decades of experience, we can point out the two most important computer security methodologies as follows.
- Detection of intrusion
- Looking for attack progress
- Patterns of network traffic
- Events like system calls
- Discovering alterations of the system (tripwire)
- Looking for attack progress
- Prevention of intrusion
- Security of the system
- Detecting and removing the faults in buffer overflow
- Firewall
- Restricting the packet flow
- Security of the system
There are a lot of other methods for enhancing the safety of computer networks, based on which we found answers for many of the questionable provisions in network security. Now let us now discuss the topmost techniques used in network security.
TOP 7 COMPUTER NETWORK SECURITY TECHNOLOGIES
We have gained expertise in using the top advanced technologies to ensure computer network security project ideas, as listed below.
- Artificial intelligence
- Statistical learning methods
- Preventing loss of data
- Blockchain technology
- Game theory
- Firewall (physical and virtual)
- Management of security events
COMPUTER NETWORK RISKS
As the air is the medium of communication in wireless technology, it works on the basis of radio communication transmission. Accessing the network becomes easy for attackers to enter into the network, breaking the security like passwords. Similar to security, the following are the research problems that impact the performance of wireless networks. What are the common computer network security threats? Let us look into computer network risks in the following section.
- Speed of transmission: In networks of large size, the transmission speed can become slower. Fibre – optic and wired networks are used to overcome this issue
- Coverage: wireless Coverage is not very broad in steel structures. As a result black spots arise at places of signal unavailability
- Interference issues: when more users are included in the network, interference occurs. Networks that are wired also impact the wireless. Communication abilities losses happen due to wireless network interference.
You can approach our guidance facility under the computer security project ideas arm to get technical support on the above-mentioned techniques.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
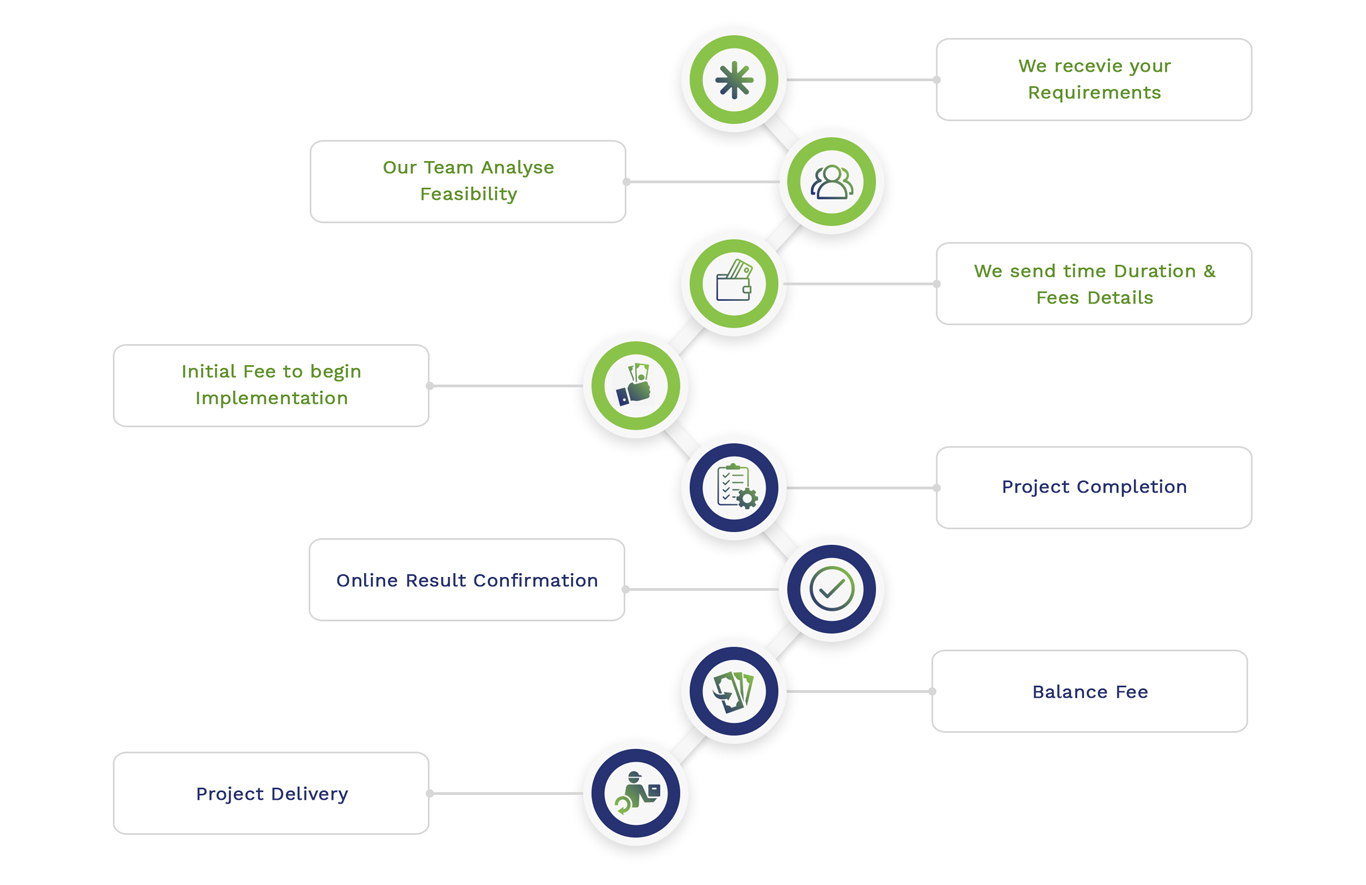
Simulation Projects Workflow
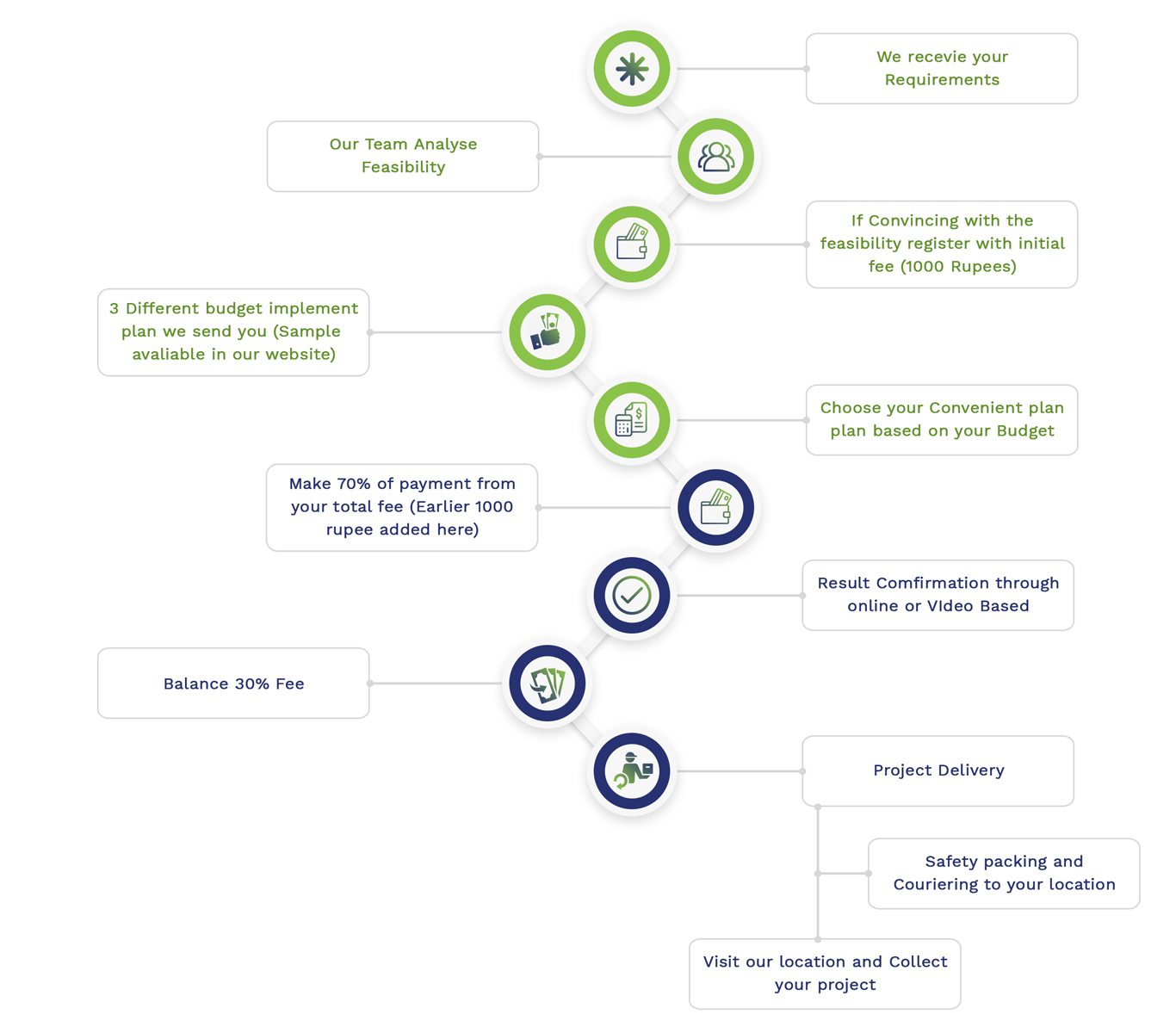
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2







