In the contemporary years, there are several networking research topics that are emerging. We handle all kinds of Networking Research Topics for PhD students. If you’re struggling to make progress, reach out to us and we’ll brainstorm fresh ideas and conduct top-notch simulations. Together with recommendations for parameters that might be utilized for comparison and exploration, the following are numerous progressive networking research topics:
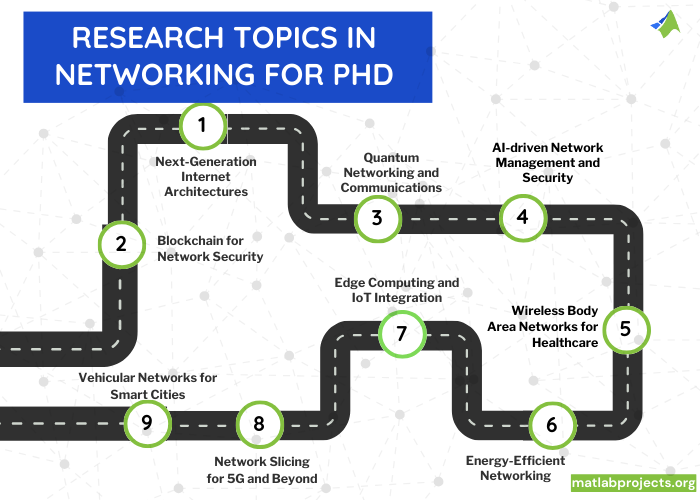
- Next-Generation Internet Architectures
- Explanation: Concentrating on safety, effectiveness, and scalability, aim to research new internet infrastructures that might substitute or essentially modify the recent TCP/IP framework.
- Parameters for Comparison: Latency, energy utilization, scalability parameters, throughput, risk evaluation, and data overhead.
- Quantum Networking and Communications
- Explanation: Encompassing quantum repeaters and quantum key distribution (QKD), investigate the advancement of quantum networking for ultra-secure interaction channels.
- Parameters for Comparison: Transmission distance, key generation levels, quantum bit error rates (QBER), secure key level, and scalability of the quantum network.
- AI-driven Network Management and Security
- Explanation: Mainly, for dynamic network management and improved protection, focus on utilizing machine learning (ML) and artificial intelligence (AI) methods encompassing automated response models and anomaly identification.
- Parameters for Comparison: False positive/ negative rates, computational overhead, detection precision, response time, and flexibility to novel attacks.
- Wireless Body Area Networks (WBANs) for Healthcare
- Explanation: Concentrating on energy effectiveness, data precision, and confidentiality-preserving data transmission, it is approachable to research the purpose of WBANs for remote health tracking.
- Parameters for Comparison: Data precision, user mobility influence, energy utilization, confidentiality preservation effectiveness, and data transmission level.
- Energy-Efficient Networking
- Explanation: For decreasing the energy utilization of network architectures involving wireless network, end-user devices, and data centers, it is appreciable to construct appropriate mechanisms and policies.
- Parameters for Comparison: Energy utilization, carbon footprint, network performance parameters such as latency throughput, and power usage effectiveness (PUE).
- Edge Computing and IoT Integration
- Explanation: In order to improve processing momentum, enhance data confidentiality, and decrease delay, aim to examine the incorporation of edge computing with IoT devices.
- Parameters for Comparison: Data processing speed, privacy protection rate, latency, bandwidth utilization, and energy usage.
- Network Slicing for 5G and Beyond
- Explanation: It is significant to research network slicing approaches in 5G networks and possible applications for different kinds of services such as URLLC, mMTC, and eMBB.
- Parameters for Comparison: Throughput, consistency, latency, resource allotment efficacy, and slice segregation performance.
- Vehicular Networks (VANETs) for Smart Cities
- Explanation: Specifically, for congestion management, protection, and vehicle-to-everything (V2X) interaction in smart cities, focus on researching the implementation and enhancement of VANETs.
- Parameters for Comparison: Message distribution speed, system scalability, communication delay, and influence on congestion effectiveness and protection.
- Software-Defined Networking (SDN) for Multi-Access Edge Computing (MEC)
- Explanation: Concentrating on dynamic resource allotment, network adaptability, and virtualization performance, investigate the contribution of SDN in handling MEC platforms.
- Parameters for Comparison: Resource usage level, operational expense, network arrangement time, and network effectiveness under differing workloads.
- Blockchain for Network Security and Management
- Explanation: Particularly, in improving network protection, network management, and decentralized network management, aim to examine the application of blockchain technology.
- Parameters for Comparison: Safety incident response time, transaction throughput, consensus latency, and overhead initiated by incorporation of blockchain.
What are the research topics in cryptography and network security?
Based on network security and cryptography domains, there are many research topics. Along with a short explanation, we offer numerous recent and progressing study topics in the discipline of network safety and cryptography:
- Post-Quantum Cryptography
- Explanation: To protect from quantum computers-based assaults, which have the ability to interrupt most of the cryptographic models that are presently being employed, construct cryptographic methods.
- Blockchain and Distributed Ledger Technologies
- Explanation: Encompassing smart contract protection, consensus technologies, and confidentiality-preserving approaches for distributed ledgers, aim to investigate the safety factors of blockchain technology.
- Homomorphic Encryption
- Explanation: Providing a method to conserve confidentiality in cloud computing and data analytics, facilitate calculations on encrypted data without requiring to decrypt it previously.
- Zero-Knowledge Proofs
- Explanation: It is approachable to create suitable algorithms including applications in confidentiality-preserving authentication, blockchain, and more, that enable one party to demonstrate to another that a description is true without exposing data over the credibility of the description itself.
- Quantum Key Distribution (QKD)
- Explanation: To protect communication channels, focus on employing quantum mechanics standards that have the capability to permit two parties to create a shared random secret key that is familiar only to them. This key is utilized further to encrypt and decrypt messages.
- Secure Multi-Party Computation (MPC)
- Explanation: Mainly, for parties to collaboratively execute an operation over their inputs when sustaining those inputs privately, aim to develop suitable algorithms. These are helpful in distributed decision-making and confidentiality-preserving data analysis.
- Advanced Persistent Threats (APTs) and Cyber Espionage
- Explanation: To identify, reduce, and protect against APTs, it is better to research policies. Generally, APTs are complicated, extended cyberattacks that are intended mainly in robbing data from aimed companies or firms.
- IoT Security
- Explanation: Involving protecting device communication and data, handling device upgrades, and assuring confidentiality, it is appreciable to solve the safety limitations of the Internet of Things (IoT).
- Biometric Security
- Explanation: It is approachable to improve the protection of biometric identification algorithms encompassing facial recognition, iris scans, and fingerprint. Aim to solve the problems of unfairness, confidentiality, and spoofing.
- Side-Channel Attacks and Countermeasures
- Explanation: Consider the interpretation and reduction of side-channel assaults that contain the ability to manipulate data that are obtained from the realistic deployment of a computer framework like power utilization, electromagnetic leaks, timing information, etc.
- Machine Learning and AI in Cybersecurity
- Explanation: To enhance cybersecurity criterions, involving malware analysis, predictive safety, and intrusion detection systems, aim to manipulate artificial intelligence and machine learning.
- Mobile and Wireless Security
- Explanation: The safety of wireless networks and mobile devices such as secure interaction protocols, mobile malware, and confidentiality problems has to be concentrated.
- Secure Software Development
- Explanation: In order to solve safety problems in the life cycle of software development, focus on constructing tools and methodologies for the structuring and development of software that is protective by structure.
- Privacy-Enhancing Technologies (PETs)
- Explanation: In order to assist persons to secure their individual data and sustain confidentiality over the internet and in electronic interactions, it is beneficial to develop mechanisms and technologies.
Research Ideas in Networking For PhD
Discover cutting-edge networking research ideas for your PhD with us! With over 18 years of experience in the field, we guarantee good results no matter what concept or idea you bring to the table. Trust matlabprojects.org for plagiarism-free thesis writing services.
- Optimized link state routing protocol performance in flying ad-hoc networks for various data rates of Un manned aerial network
- A filter model for intrusion detection system in Vehicle Ad Hoc Networks: A hidden Markov methodology
- A link-state QoS routing protocol based on link stability for Mobile Ad hoc Networks
- A light-weight trust-based QoS routing algorithm for ad hoc networks
- A stochastic approach for packet dropping attacks detection in mobile Ad hoc networks
- Broadcast Expenses Controlling Techniques in Mobile Ad-hoc Networks: A Survey
- A detailed study of a CDMA based approach to enhance ad hoc network performance
- Computationally efficient privacy preserving anonymous mutual and batch authentication schemes for vehicular ad hoc networks
- A novel Intrusion Detection System for Vehicular Ad Hoc Networks (VANETs) based on differences of traffic flow and position
- Energy-efficient MAC in ad-hoc networks inspired by conflict resolution concepts
- Threshold cryptography in mobile ad hoc networks under minimal topology and setup assumptions
- Effective link quality estimation as a means to improved end-to-end packet delivery in high traffic mobile ad hoc networks
- A survey of MAC layer solutions to the hidden node problem in ad-hoc networks
- Analytical and simulative performance evaluation of cluster-based multihop ad hoc networks
- A stable weight-based on-demand routing protocol for mobile ad hoc networks
- Performance evaluation of a multilevel hierarchical location management protocol for ad hoc networks
- An accurate and precise malicious node exclusion mechanism for ad hoc networks
- Impact of the routing protocol choice on the Envelope-Based Admission Control scheme for ad hoc networks
- Protecting data flow anonymity in mobile ad hoc networks that employ cooperative caching
- DIMH: A novel model to detect and isolate malicious hosts for mobile ad hoc network
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
Simulation Projects Workflow
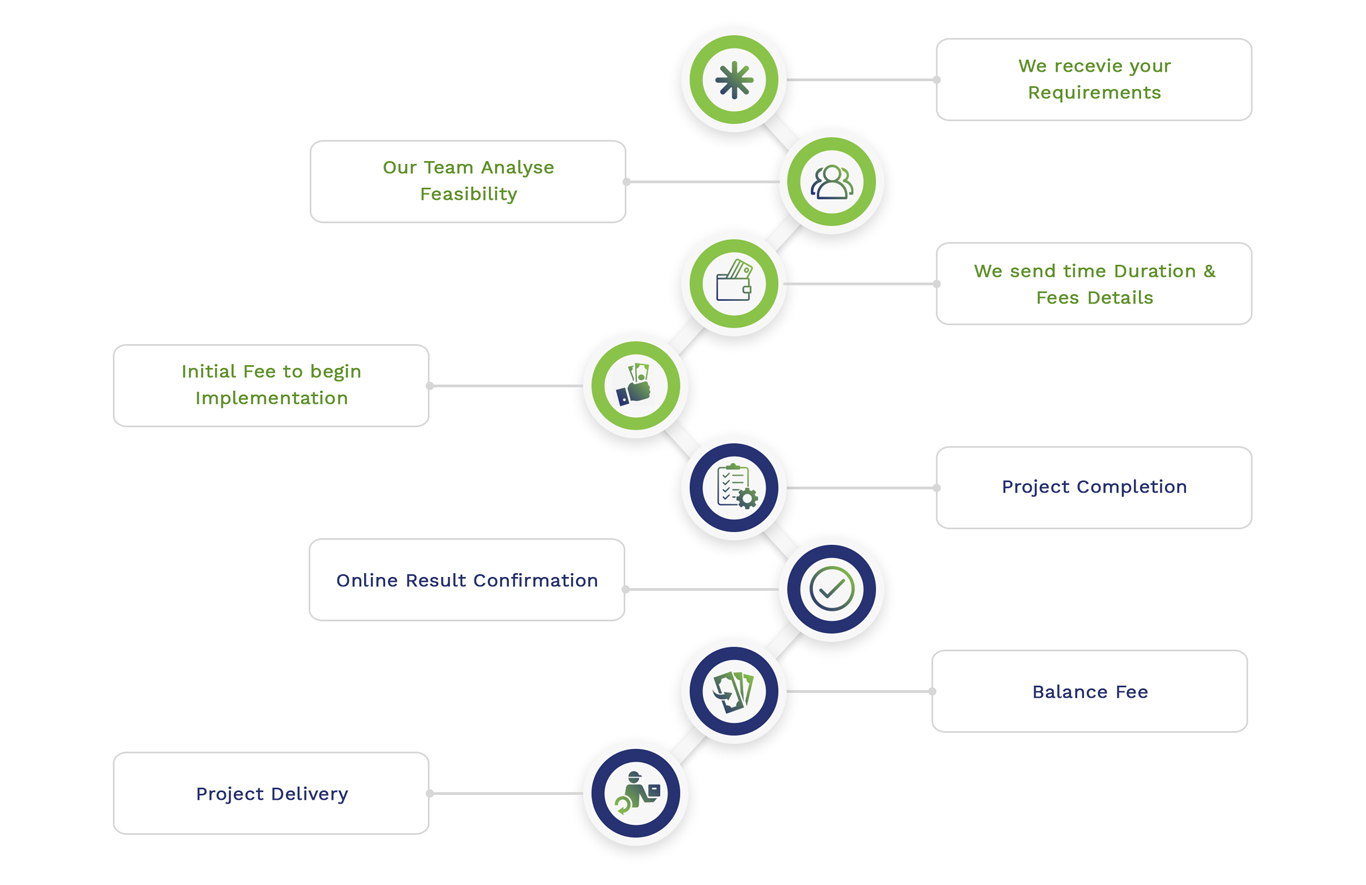
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






