PROJECTS ON CRYPTOGRAPHY
Projects on cryptography can be implemented for securely transmitting information’s between two parties (sender and receiver). Cryptography is the process of converting plain text into cipher text at the sender with the help of substitution methods and ciphering algorithms and converting cipher text into plain text at the receiver side using same substitution methods and ciphering algorithms. Three independent dimensions of cryptographic systems are,
- Number of keys used.
- Transforming plain text into cipher text based on different operations.
- Process way of plain text.
Projects on Cryptography should be implemented based on some security services. The services are integrity, confidentiality, non-repudiation, Authentication, access control and availability. Integrity has the types of data integrity and system integrity. In data integrity information changes has been made by the authorized person only. In system integrity avoid unauthorized manipulation of the system by performing intended functions in an unimpaired manner. Confidentiality is the process of protecting private information’s in secured manner. It has the types of data confidentiality and privacy. In non-repudiation process the sender and receiver not able to deny transmission. Authentication ensures the process of identity of the original content. Access control must do the process of controlling information resources. Availability check the system works in proper manner and the services are not refusing to the authorized persons.
Projects on Cryptography will depend on some security and cryptographic attacks. The security attacks are interception, fabrication, interruption and modification. Cryptographic attacks are classified into two types such as active attacks and passive attacks. Passive attacks are done the process of eavesdropping on the transmission. It has two types named as traffic analysis and release of message contents. In traffic analysis the protection can be made between sender and receiver by using encryption pattern of the message. In release of message content the conversation of mail and telephone could be made. Here, the transformation information’s are kept confidential for both conversations. Active attacks are do some modification process onto the generation of false flow and data flow. It can be classified into four types. There are replay, denial of service, masquerade and modification of messages.
Normally, a key can play the important role in cryptography process because without secret key we are not transferring secured information between two parties. The key can be generated with the help of cryptographic algorithms are called as symmetric and asymmetric. Symmetric key means both sender and receiver can use same key for encryption and decryption. Asymmetric key means both sender and receiver could use different keys for encryption and decryption. The cryptographic algorithms are used to make unreadable format of information to the unauthorized or malware users.
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
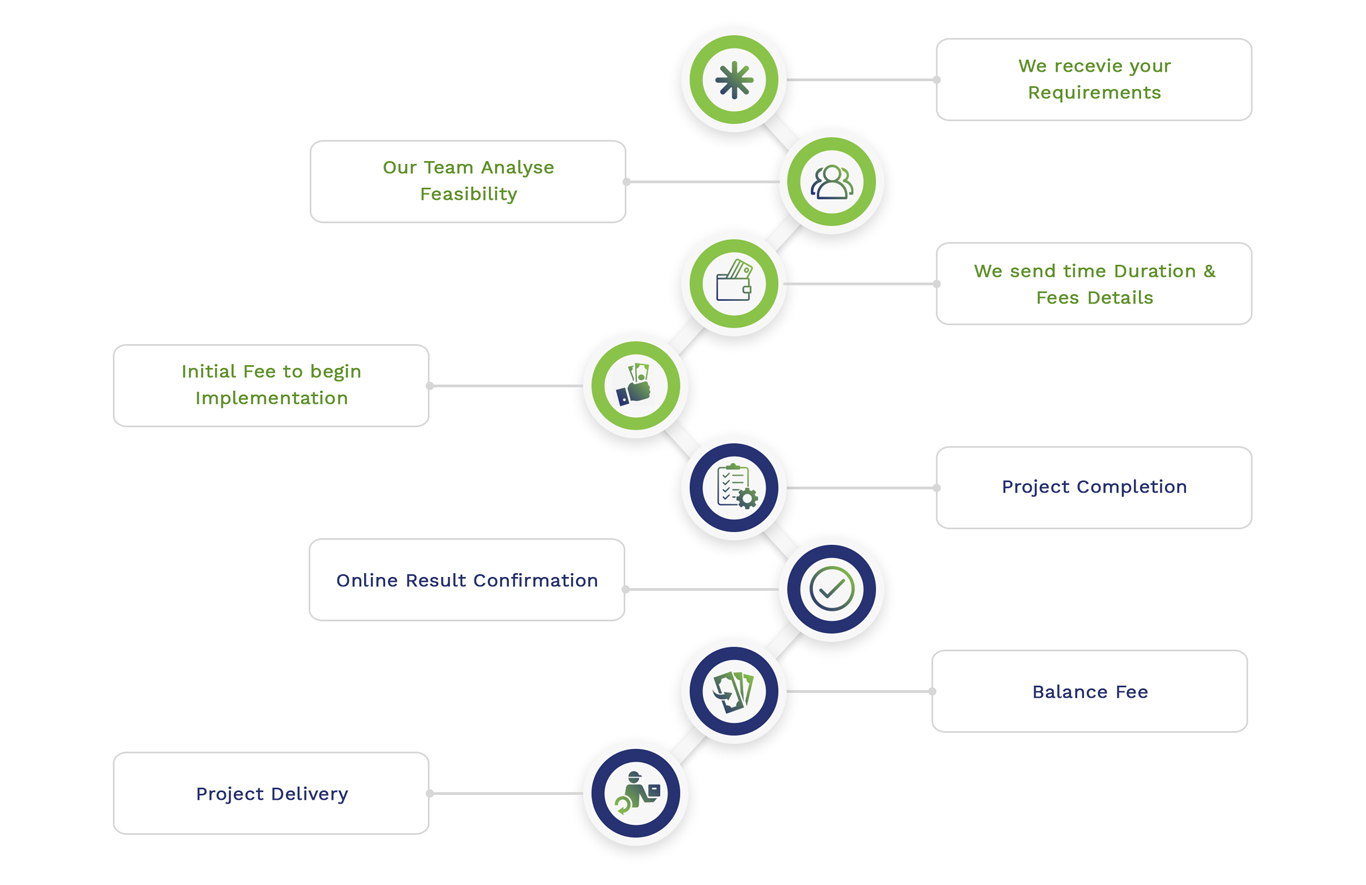
Simulation Projects Workflow
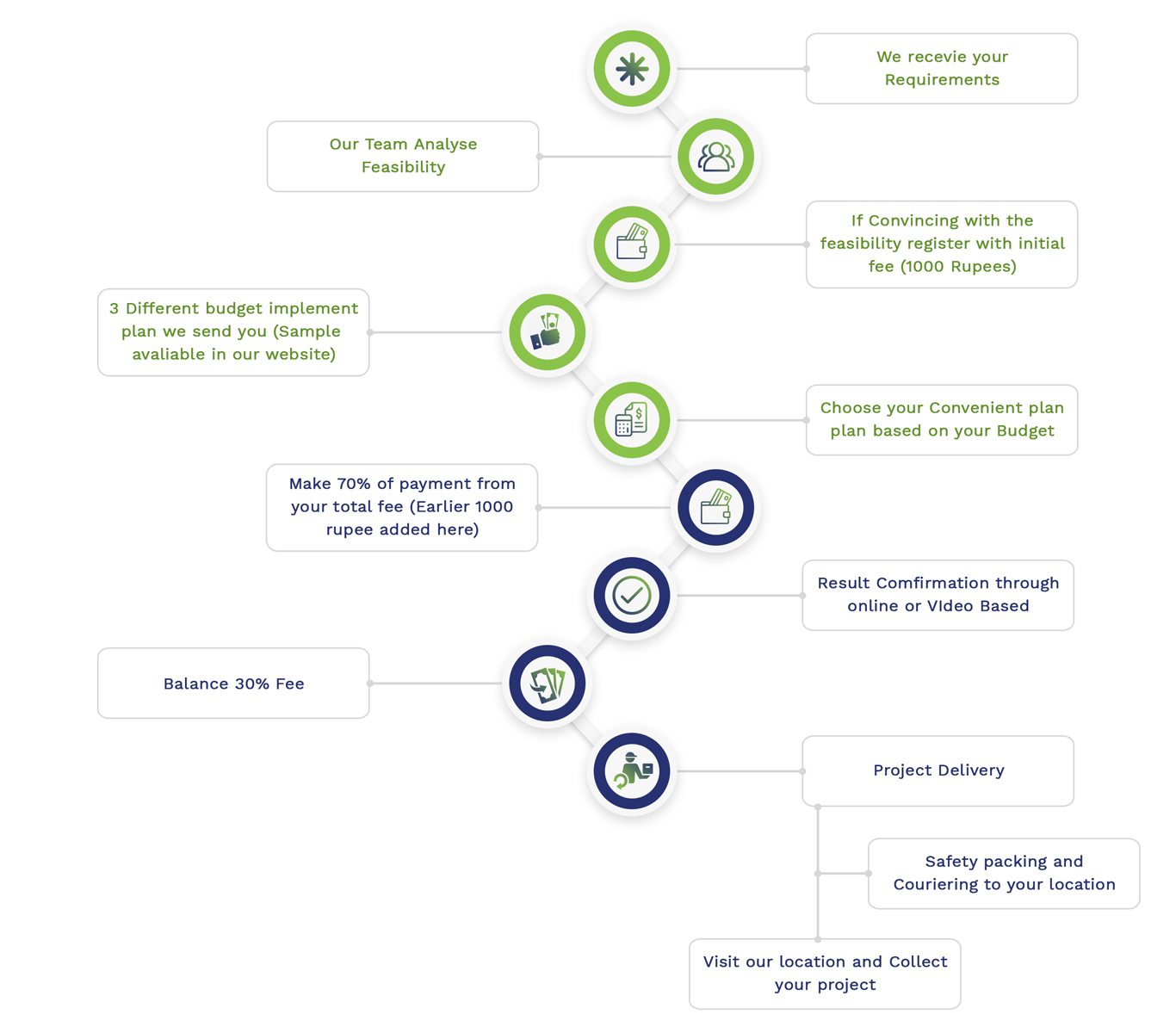
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






