In the contemporary years, there are several research topics that are progressing in the domain of cybersecurity. We are experts in research field for past 16+ years and have won research success for more than 8000+ scholars. Join us today to gain triumph for your research work. By providing chances for creative study and important aspects, the following are numerous Research Topics In Computer Networks And Security that grasp the recent patterns and limitations in research domain:
- Advanced Persistent Threats (APTs) Detection and Mitigation
- In order to identify and reduce complicated, longstanding cyber threats that are arranged by extremely trained challengers intending particular firms, concentrate on constructing suitable policies and mechanisms.
- Quantum Cryptography and Post-Quantum Cryptography
- Encompassing the advancement and exploration of quantum-resilient methods and protocols, investigate cryptographic algorithms that are safe against quantum computing assaults.
- Machine Learning and AI in Network Security
- The application of machine learning and artificial intelligence approaches should be examined to enhance network safety, incorporating threat intelligence analysis, autonomous incident response, and anomaly identification.
- Blockchain for Network Security
- Concentrating on the applications like safer DNS protocols, morality validation, and decentralized identity management, research the capability of blockchain technology in improving the safety of computer networks.
- IoT Security and Privacy
- In the Internet of Things (IoT) environments, solve the safety and confidentiality limitations by creating strong authentication technologies, safer interaction protocols, and confidentiality-preserving data collection algorithms.
- Wireless Network Security
- With the concentration on protecting wireless interaction channels and securing against eavesdropping and spoofing attacks, it is appreciable to investigate novel attacks and protection technologies in wireless networking, incorporating Bluetooth, 5G technologies, and Wi-Fi.
- Software-Defined Networking (SDN) Security
- Encompassing the security of the SDN control plane, safer network virtualization, and SDN-related safety services, investigate safety limitations and approaches in software-defined networking platforms.
- Secure Cloud Computing
- Specifically, in cloud computing architectures, aim to explore safety problems involving multi-tenancy vulnerabilities, data confidentiality, and safe cloud source offering and handling.
- Cyber-Physical Systems (CPS) Security
- Solving certain attacks and constructing incorporated safety approaches, concentrate on the safety of cyber-physical models, like smart grids, automated vehicles, and business control frameworks.
- Privacy-enhancing Technologies
- Encompassing anonymous interaction frameworks, differential privacy, and zero-knowledge evidence, research technologies and protocols that improve user confidentiality in virtual interactions and dealings.
- Network Forensics and Incident Response
- Concentrating on the detection, exploration, and reduction of cyber incidents in complicated network platforms, create algorithms and tools for efficient network forensics and incident response.
- Secure Mobile Communications
- In mobile computing and interaction, solve safety and confidentiality problems, incorporating safer mobile app advancement, security against mobile malware, and confidentiality-preserving mobile monitoring models.
- Edge Computing Security
- Determining data morality, privacy, and safe computation at the edge of the network, investigate safety limitations in edge computing infrastructures.
- Cross-domain Security Policies and Models
- Among various fields and administrative restrictions, research systems and models for explaining and applying safety strategies, thereby assuring reliable safety measures in cooperative platforms.
What are the top 5 emerging cyber security challenges?
Cybersecurity limitations become significantly complicated and difficult, due to the progression of digital prospects. Below we describe the topmost evolving cybersecurity-based limitations:
1. Ransomware Evolution and Proliferation
Intending not simply on particular models but also on complete networks and data centers encompassing cloud architecture, ransomware assaults have become more complicated. Hazardous to release complicated data in a public manner without getting affected by ransom, attackers are also manipulating double extortion approaches. The emerging attacks and complication of ransomware struggles are emphasized by the transition to focusing on domains such as academic universities, essential architecture, and healthcare.
2. Supply Chain Attacks
In order to implement risks in minimum safer components of a firm’s environment, cyber assaulters are significantly intending the supply chain. Generally, the assaulters can get the permission to access the networks of numerous firms at the same time by convincing a service supplier or single provider. A best example is the SolarWinds attack, where malevolent code was appended into software upgrades, thereby impacting thousands of industries and government agencies. The combined actions and improved safety criterions among the whole supply chain are needed to solve these risks.
3. Quantum Computing Threat to Encryption
Encompassing ECC and RSA, the approach of quantum computing demonstrates an important attack to recent encryption principles that can be harmed in an easy way by adequately robust quantum computers. In the upcoming, every recent secure virtual interaction is susceptible to being decrypted in digital manner. To protect complicated data in opposition to upcoming quantum assaults, the advancement and standardization of quantum-resilient cryptography are determined as significant.
4. AI and Machine Learning-Based Attacks
Artificial intelligence (AI) and machine learning (ML) mechanisms develop novel cyber-attacks, as they become more complicated. To computerize the formation and execution of assaults, generally the assaulters are employing AI and ML, therefore making them more efficient and problematic to identify. These mechanisms computerized risk detection, facilitate adaptive malware, and complicated phishing struggles utilizing deep fakes. Although AI and ML have the capability to improve cybersecurity protection, they also initiate novel risks and moral problems.
- IoT Security Vulnerabilities
Normally, the attack surface for cyber attacks is extensively extended by the enormous growth of Internet of Things (IoT) devices. The assaulters are intending to intrude networks or develop botnets for DDoS assaults, as most of the IoT devices are constructed with minimum safety characteristics. Usually, better understanding between manufacturers and users regarding the significance of IoT safety and novel techniques and principles are needed to protect these devices.

Research Ideas in Computer Networks and Security
Embark on a quest for knowledge as we uncover the hidden gems of computer networks and security. Our team of experts is dedicated to bringing forth novel computer networks and security ideas and groundbreaking research in this fascinating field. Join us as we unravel the mysteries and pave the way for future advancements in computer networks and security tailored to your needs.
- Multi-Agent Approach for Enhancing Security of Protection Schemes in Cyber-Physical Energy Systems
- Cyber-Physical Security Assessment and Resilience of a Microgrid Testbed
- Cyberattack Ontology: A Knowledge Representation for Cyber Supply Chain Security
- Enhancing cyber physical system security via anomaly detection using behaviour analysis
- Adoption of Cloud-Cyber Security: Challenges and Perceptions Within Resource Constrained Higher Education Institutions
- A Bootstrapping Approach for Developing a Cyber-security Ontology Using Textbook Index Terms
- Semantic data integration in upgrading hydro power plants cyber security
- A system-aware cyber security method for shipboard control systems with a method described to evaluate cyber security solutions
- The Complexity of the Infinity Replacement Problem in the Cyber Security Model
- Cybers Security Analysis and Measurement Tools Using Machine Learning Approach
- Cyber-Physical System Security Surveillance using Knowledge Graph based Digital Twins – A Smart Farming Usecase
- A Cyber-Security Methodology for a Cyber-Physical Industrial Control System Testbed
- Analysis of Cyber-Attack in Big Data IoT and Cyber-Physical Systems – A Technical Approach to Cybersecurity Modeling
- A Survey on Security Communication and Control for Smart Grids Under Malicious Cyber Attacks
- A cyber-physical integrated security framework with fuzzy logic assessment for cultural heritages
- SentinelPlus: A Cost-Effective Cyber Security Solution for Healthcare Organizations
- Cyber-Security Assessment of Power System Digital Components in the Conditions of Hostilities
- A Proposed Cyber security framework for auditing in financial institutions
- Cyber Security challenges and Issues of Industrial Control Systems–Some Security Recommendations
- Improvement of cyber-security measures in National Grid SA substation process control
Subscribe Our Youtube Channel
You can Watch all Subjects Matlab & Simulink latest Innovative Project Results
Our services
We want to support Uncompromise Matlab service for all your Requirements Our Reseachers and Technical team keep update the technology for all subjects ,We assure We Meet out Your Needs.
Our Services
- Matlab Research Paper Help
- Matlab assignment help
- Matlab Project Help
- Matlab Homework Help
- Simulink assignment help
- Simulink Project Help
- Simulink Homework Help
- Matlab Research Paper Help
- NS3 Research Paper Help
- Omnet++ Research Paper Help
Our Benefits
- Customised Matlab Assignments
- Global Assignment Knowledge
- Best Assignment Writers
- Certified Matlab Trainers
- Experienced Matlab Developers
- Over 400k+ Satisfied Students
- Ontime support
- Best Price Guarantee
- Plagiarism Free Work
- Correct Citations
Expert Matlab services just 1-click

Delivery Materials
Unlimited support we offer you
For better understanding purpose we provide following Materials for all Kind of Research & Assignment & Homework service.
 Programs
Programs Designs
Designs Simulations
Simulations Results
Results Graphs
Graphs Result snapshot
Result snapshot Video Tutorial
Video Tutorial Instructions Profile
Instructions Profile  Sofware Install Guide
Sofware Install Guide Execution Guidance
Execution Guidance  Explanations
Explanations Implement Plan
Implement Plan
Matlab Projects
Matlab projects innovators has laid our steps in all dimension related to math works.Our concern support matlab projects for more than 10 years.Many Research scholars are benefited by our matlab projects service.We are trusted institution who supplies matlab projects for many universities and colleges.
Reasons to choose Matlab Projects .org???
Our Service are widely utilized by Research centers.More than 5000+ Projects & Thesis has been provided by us to Students & Research Scholars. All current mathworks software versions are being updated by us.
Our concern has provided the required solution for all the above mention technical problems required by clients with best Customer Support.
- Novel Idea
- Ontime Delivery
- Best Prices
- Unique Work
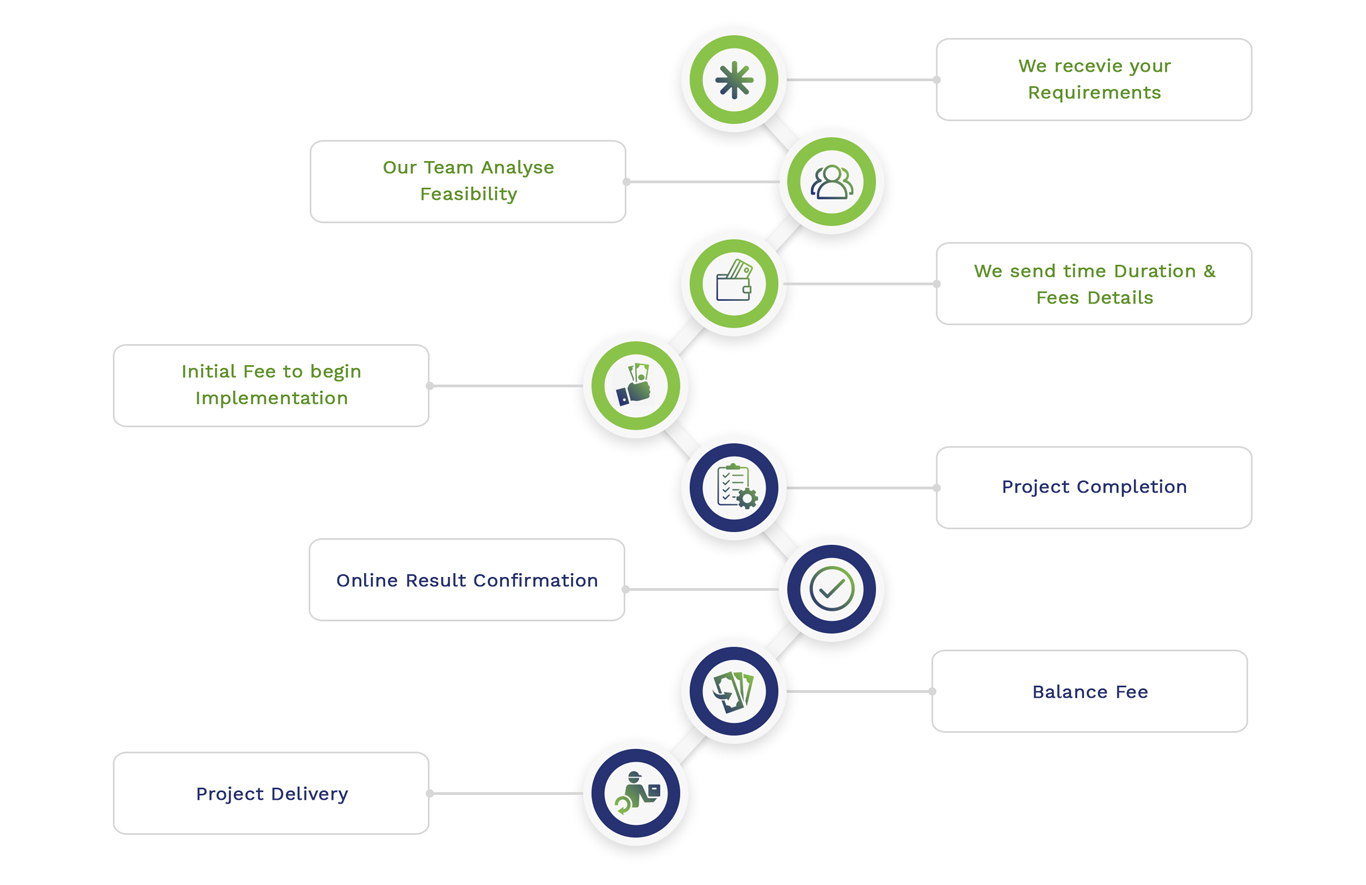
Simulation Projects Workflow
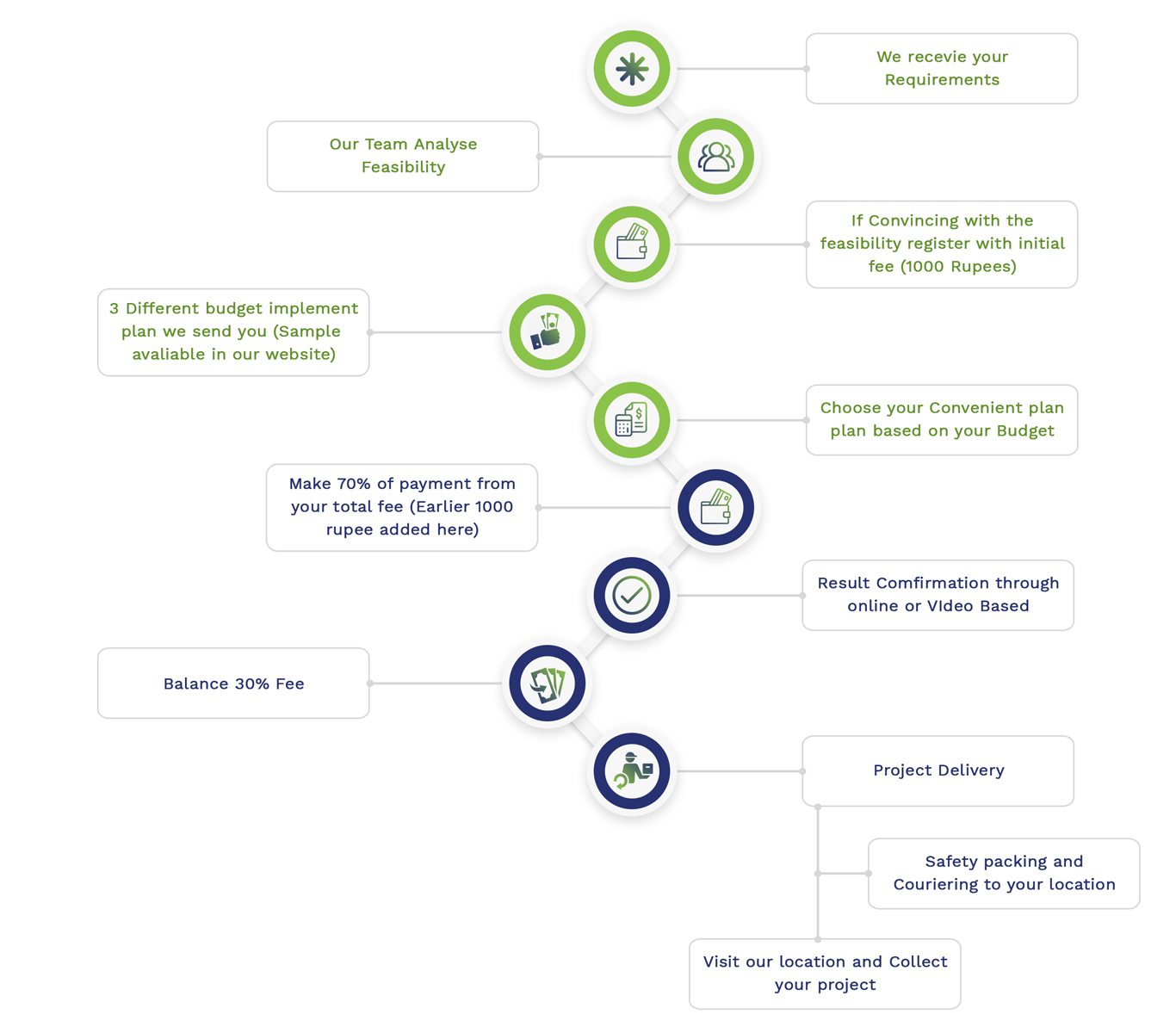
Embedded Projects Workflow


 Matlab
Matlab Simulink
Simulink NS3
NS3 OMNET++
OMNET++ COOJA
COOJA CONTIKI OS
CONTIKI OS NS2
NS2






